See-SURF – Python based scanner to find potential SSRF parameters
January 15, 20255 min read
January 14, 2024By Prapattimynk
PyWebCopy is a free tool for copying full or partial websites locally onto your hard-disk for offline viewing. https://github.com/rajatomar788/pywebcopy/ PyWebCopy will scan the specified website and download its content onto your hard-disk. Links to resources such as style-sheets, images, and other pages in the website will automatically be remapped to match the local path. Using
January 14, 2024By Prapattimynk
https://github.com/Stirling-Tools/Stirling-PDF This is a powerful locally hosted web based PDF manipulation tool using docker that allows you to perform various operations on PDF files, such as splitting merging, converting, reorganizing, adding images, rotating, compressing, and more. This locally hosted web application started as a 100% ChatGPT-made application and has evolved to include a wide range
January 14, 2024By Prapattimynk
https://github.com/openrewrite/rewrite The OpenRewrite project is a mass source code refactoring ecosystem. Reduce 1000s of hours of static code analysis fixes to minutes. Turn a four-month migration project into four hours of work. Patch security vulnerabilities across 100s of repositories at once. OpenRewrite automates code refactoring and remediation tasks for you, enabling developers to deliver more
January 14, 2024By Prapattimynk
https://github.com/Aditya-dom/moonwalk-back Cover your tracks during Linux Exploitation by leaving zero traces on system logs and filesystem timestamps. moonwalk-back is a 400 KB single-binary executable that can clear your traces while penetration testing a Unix machine. It saves the state of system logs pre-exploitation and reverts that state including the filesystem timestamps post-exploitation leaving zero traces of a ghost in
January 14, 2024By Prapattimynk
https://github.com/cryptpad/cryptpad CryptPad is a collaboration suite that is end-to-end-encrypted and open-source. It is built to enable collaboration, synchronizing changes to documents in real time. Because all data is encrypted, the service and its administrators have no way of seeing the content being edited and stored. CryptPad offers a variety of collaborative tools that encrypt your
January 14, 2024By Prapattimynk
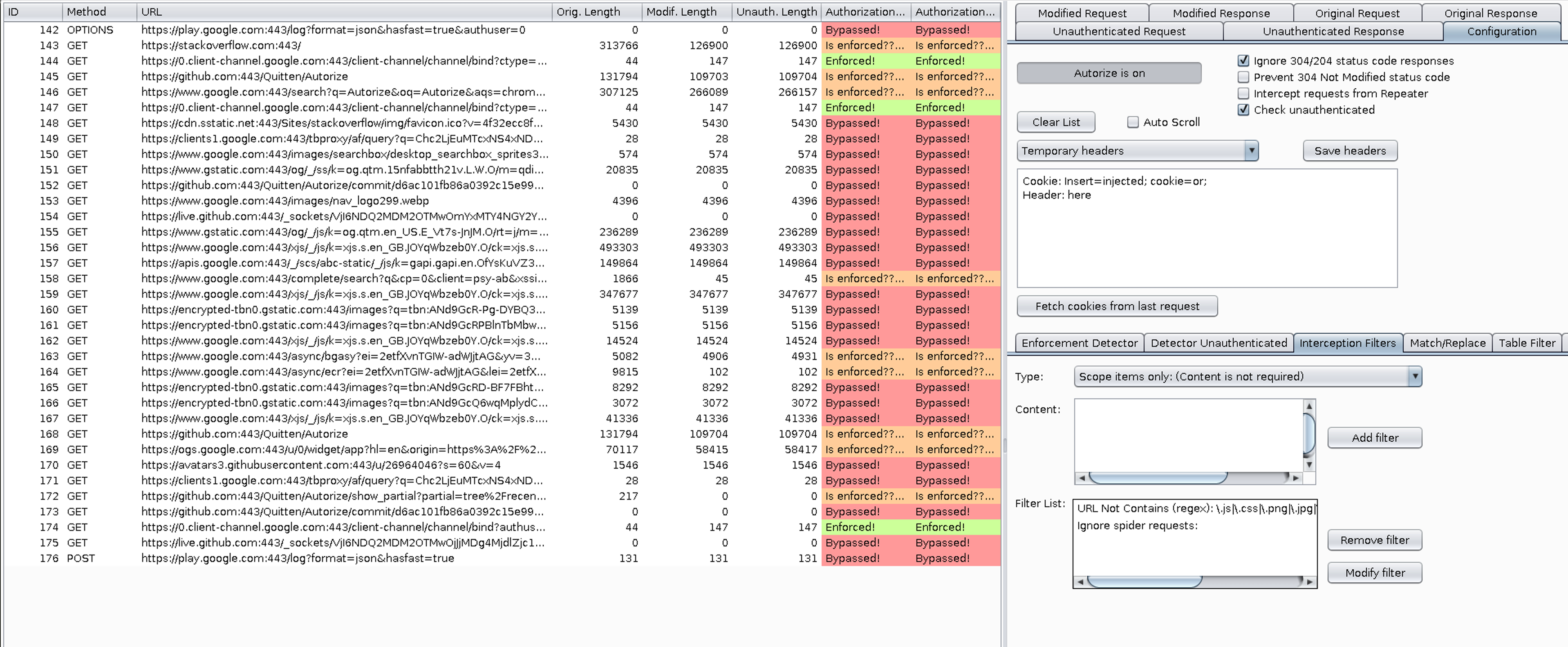
https://github.com/Quitten/Autorize Autorize is an automatic authorization enforcement detection extension for Burp Suite. It was written in Python by Barak Tawily, an application security expert. Autorize was designed to help security testers by performing automatic authorization tests. With the last release now Autorize also perform automatic authentication tests. Installation User Guide – How to use? Authorization
January 14, 2024By Prapattimynk
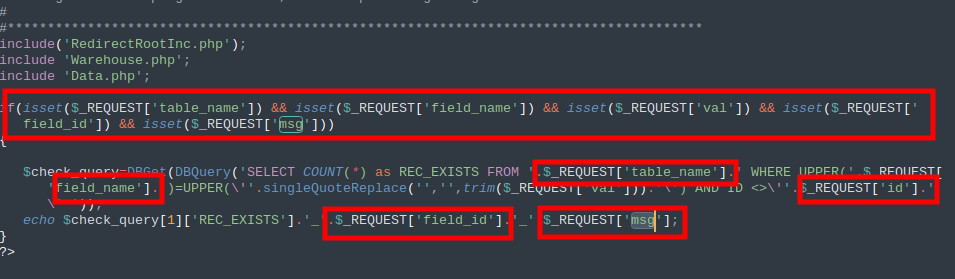
SQL injection is a common web application vulnerability that allows an attacker to manipulate the SQL queries executed by the application’s database. This can lead to unauthorized access, data leakage, and even complete compromise of the application and its underlying infrastructure. In this article, we will focus on one particular type of SQL injection known
January 14, 2024By Prapattimynk
https://github.com/Mxcoders2s/Slient-Url-Exploit-Slient-Builder-Exploit-Database-Cve-2023-Malware URL Contamination (Muted Java Drive-By) URL Contamination Exploit Muted Java Drive-By downloads can transpire during the act of perusing a website, inaugurating an electronic mail communication. It might even occur through engaging with a malevolent pop-up interface: enticed by the illusion that it pertains to an error dossier from the operating system of the
January 14, 2024By Prapattimynk
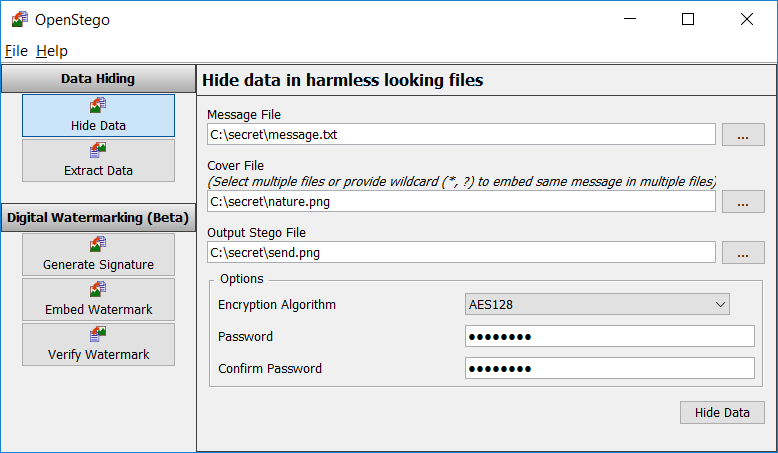
https://github.com/syvaidya/openstego OpenStego is a steganography application that provides two functionalities: a) Data Hiding: It can hide any data within an image file. b) Watermarking: Watermarking image files with an invisible signature. It can be used to detect unauthorized file copying. OpenStego is a steganography application that provides two functionalities: Usage For GUI: Use menu shortcut
November 16, 2023By Prapattimynk
For the purposes of this article, I would like to distinguish two topics: Vulnerability Details describing single security issue raised as a part of bigger report or bug bounty activities; A Formal Vulnerability Report is created as a result of security assessments and may contain more than one vulnerability. Vulnerability details describes single security issue or
July 30, 2023By Prapattimynk
Welcome to our blog, “Top 05 Footprinting and Reconnaissance Online Tools That You Should Know in 2023”! In this comprehensive guide, we will explore the cutting-edge tools and techniques used for footprinting and reconnaissance in the rapidly evolving cybersecurity landscape. Stay ahead of the game as we delve into the must-know tools that empower security
June 29, 2023By Prapattimynk
In today’s digital age, the internet serves as a vast source of information, both publicly available and hidden. Open Source Intelligence (OSINT) plays a crucial role in gathering and analyzing this data to obtain valuable insights. As we enter the year 2023, several powerful online tools have emerged, empowering individuals and organizations with advanced capabilities
June 26, 2023By Prapattimynk
Introduction In today’s digital age, our smartphones have become an integral part of our lives. We use them for communication, accessing personal and financial information, and staying connected with the world. However, this increased reliance on mobile devices also raises concerns about security. The question “Is my phone hacked?” is one that many individuals ask,
- 1
- 2
Tips
APKDeepLens artificial-intelligence ARTToolkit Audit BIBT BITB Burpsuite Bypass EDR Captcha Solver Clone Websites Digital Forensics Dnsbruter Draw2Img Email Osint error-based SQL injection Extension File Transfer Flying Carpet hacking gadgets HTML Smuggling IDOR Information Gathering Labs Linux Maltrail networking Network security Osint PDF Tool Pentesting Tool PiAlert Piper puter pyWebCopy QR File Share Scan Android SQL injection SSRF System logs Text To Voice Threat Tool Toolkit TREVORproxy Voice Clone