SQL injection is a common web application vulnerability that allows an attacker to manipulate the SQL queries executed by the application’s database. This can lead to unauthorized access, data leakage, and even complete compromise of the application and its underlying infrastructure. In this article, we will focus on one particular type of SQL injection known as error-based SQL injection, explore its exploitation techniques, discuss detection and prevention, and delve into bypassing Web Application Firewalls (WAFs).
Understanding Error-Based SQL Injection
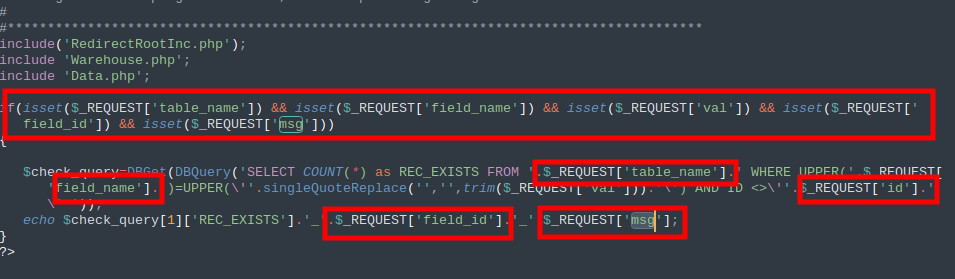
Error-based SQL injection is a technique that relies on inducing SQL errors to extract information from the database. It exploits vulnerabilities in the application’s input validation and sanitization to inject malicious SQL statements. By carefully crafting these statements, an attacker can trigger errors that reveal valuable information about the database structure, data, and even execute arbitrary commands.
Exploiting Error-Based SQL Injection
Let’s consider a simple example to illustrate how error-based SQL injection works:
SELECT * FROM users WHERE id = '1' UNION SELECT 1,2,3 FROM information_schema.tablesIn this example, the attacker injects a UNION SELECT statement to retrieve data from the information_schema.tables table. If the application is vulnerable to error-based SQL injection, it will execute the injected SQL statement, resulting in an error. The error message will contain the extracted data, which the attacker can then analyze and exploit further.
Finding and Fixing Error-Based SQL Injection
Detecting error-based SQL injection vulnerabilities requires a combination of manual testing and automated scanning tools. Here are some steps to follow:
- Identify user input fields in the application, such as search boxes, login forms, or URL parameters.
- Attempt to inject SQL statements by adding single quotes, semicolons, or other special characters to the input.
- If the application responds with error messages that reveal database-related information, it is likely vulnerable to error-based SQL injection.
- To fix the vulnerability, ensure that all user input is properly validated, sanitized, and parameterized before being used in SQL queries. Implementing prepared statements or using an Object-Relational Mapping (ORM) framework can help prevent SQL injection.
Bypassing Web Application Firewalls (WAFs)
Web Application Firewalls (WAFs) are security measures designed to detect and block malicious traffic, including SQL injection attempts. However, skilled attackers can employ various techniques to bypass WAFs and successfully exploit error-based SQL injection vulnerabilities. Here are a few methods:
- Obfuscating the injected SQL code to evade signature-based detection.
- Breaking the injection payload into multiple requests to bypass rate limiting and pattern matching rules.
- Encoding the payload using different character sets or encoding schemes to bypass input validation filters.
- Using time-based techniques to delay the execution of malicious queries, making detection more difficult.
It is crucial for organizations to regularly update their WAF rules and configurations to stay ahead of evolving attack techniques. Employing a combination of signature-based and behavioral-based detection mechanisms can enhance the effectiveness of WAFs in preventing SQL injection attacks.
Conclusion
Error-based SQL injection is a serious security vulnerability that can lead to severe consequences if left unaddressed. By understanding how this type of injection works and implementing proper detection, prevention, and WAF bypass techniques, organizations can significantly reduce the risk of SQL injection attacks. Regular security assessments, code reviews, and employee training are essential to maintain a robust defense against these threats.
Remember, securing your applications against SQL injection is an ongoing process that requires continuous monitoring and updates. By staying informed about the latest attack techniques and following best practices, you can protect your applications and data from the ever-evolving threat landscape.


What do you think?
Show comments / Leave a comment