January 15, 2025By Prapattimynk
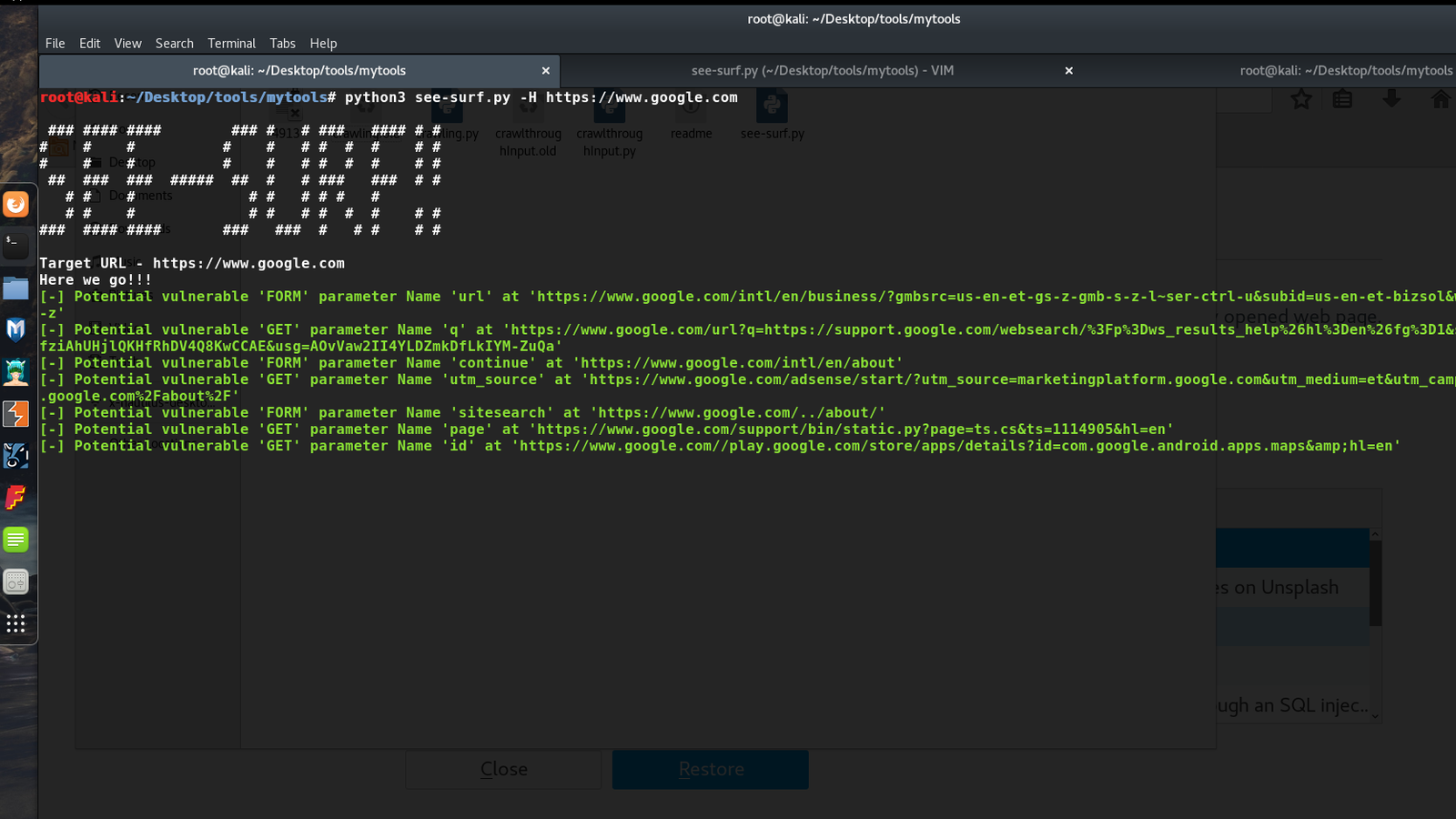
A Python based scanner to find potential SSRF parameters in a web application. See-SURF helps you detect potential SSRF parameters and validates the finding it by making a DNS/HTTP request back to your server. It can be added to your arsenal of recon while doing bug hunting/web security testing. Tech/framework used Built with Installation git
January 10, 2025By Prapattimynk
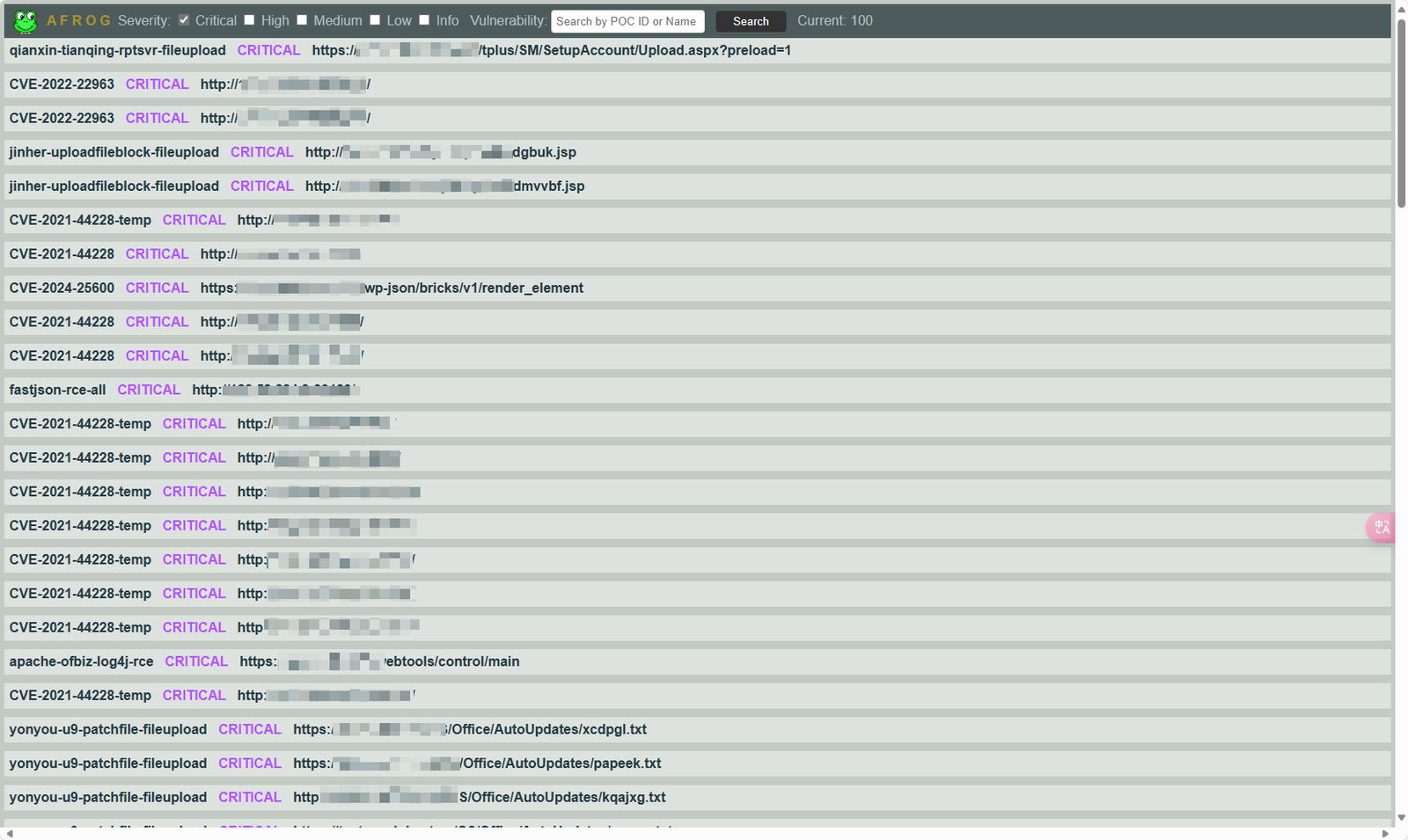
What is afrog afrog is a high-performance vulnerability scanner that is fast and stable. It supports user-defined PoC and comes with several built-in types, such as CVE, CNVD, default passwords, information disclosure, fingerprint identification, unauthorized access, arbitrary file reading, and command execution. With afrog, network security professionals can quickly validate and remediate vulnerabilities, which helps
January 6, 2025By Prapattimynk
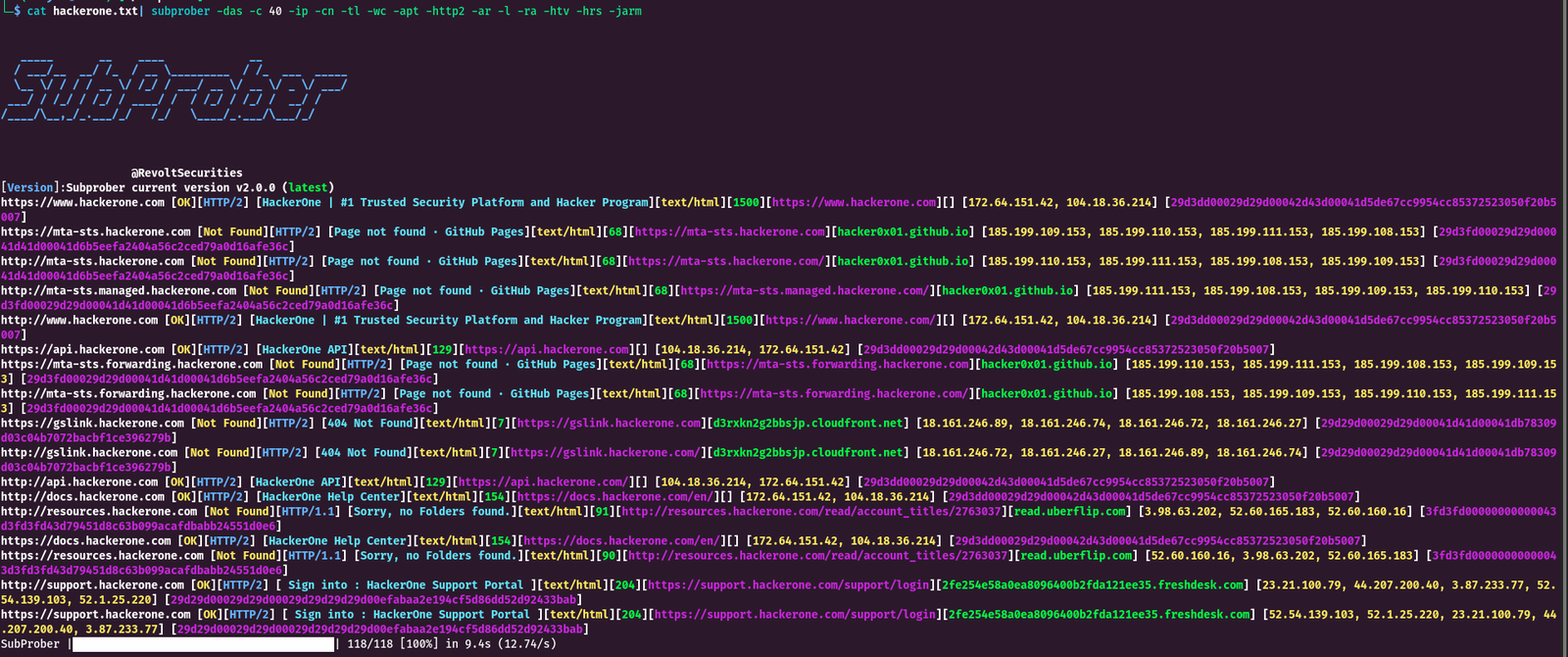
An essential HTTP multi-purpose Probing Tool for Penetration Testers and Security Researchers with Asynchronous httpx client support Overview Subprober is a powerful and efficient tool designed for penetration testers and security professionals. This release introduces several enhancements, bug fixes, and new features to elevate your probing experience. Subprober facilitates fast and reliable information extraction, making
January 5, 2025By Prapattimynk
Your malware’s favorite sandbox – where red teamers come to bury their payloads. A sandbox environment designed specifically for malware development and payload testing. This Web Application enables red teamers to validate evasion techniques, assess detection signatures, and test implant behavior before deployment in the field. Think of it as your personal LitterBox for perfecting
December 27, 2024By Prapattimynk
Software-defined networking ( SDN ) is a modern approach to network design and management that separates the control plane from the data plane. Simply put, instead of each network device (such as a router or switch) being responsible for making routing decisions, these decisions are aggregated into a central controller. 🔥 Simple explanation: Imagine a
December 27, 2024By Prapattimynk
The ARP protocol relies on mapping IP addresses to MAC addresses. In an ARP spoofing attack, an attacker sends fake ARP messages to devices on the network, claiming to have the MAC address of another device (such as a router or another computer). This misleads other devices, so their data traffic is sent to the
December 23, 2024By Prapattimynk
ZigStrike is a robust shellcode loader developed in Zig, offering a variety of injection techniques and anti-sandbox features. It leverages compile-time capabilities for efficient shellcode allocation, demonstrating proven success in bypassing advanced security solutions. ZigStrike includes a custom payload builder, allowing users to easily select and construct payloads via a web application built with Python.
December 23, 2024By Prapattimynk
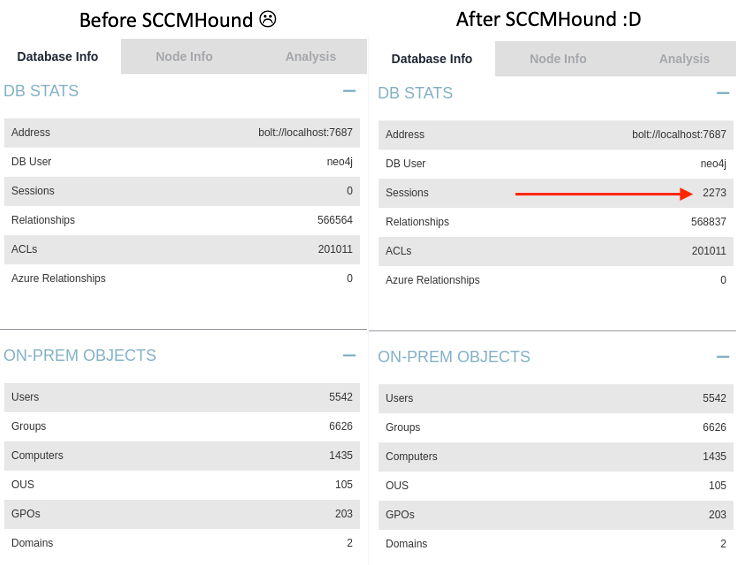
SCCMHound is a C# BloodHound collector for Microsoft Configuration Manager (MCM). If you’re looking for a way to collect BloodHound session information from Configuration Manager’s users and computers then this is the tool for you! Highly recommend importing collected data with another collector’s data (SharpHound, SOAPHound, etc.). Doesn’t matter whether it’s imported before or after
December 23, 2024By Prapattimynk
gocheck is a golang implementation of Matterpreter’s DefenderCheck that aims to aid red teams in their malware development capabilities by identifying the exact bytes in their malware that are flagged by security solutions (incomplete integration with enterprise AV, see External Scanners) I also wrote a blog post showcasing this project: Identifying Malicious Bytes in Malware
December 23, 2024By Prapattimynk
Android application that runs a local VPN service to bypass DPI (Deep Packet Inspection) and censorship. This application runs a SOCKS5 proxy ByeDPI and redirects all traffic through it. Installation <img src=”https://github.com/machiav3lli/oandbackupx/blob/034b226cea5c1b30eb4f6a6f313e4dadcbb0ece4/badge_github.png”alt=”Get it on GitHub”height=”80″><img src=”https://gitlab.com/IzzyOnDroid/repo/-/raw/master/assets/IzzyOnDroid.png”alt=”Get it on IzzyOnDroid”height=”80″> Or use Obtainium Settings To bypass some blocks, you may need to change the settings. More
December 23, 2024By Prapattimynk
Introduction to Hacking Gadgets The advent of modern technology has led to a myriad of innovations that simplify everyday tasks and enhance user experience. However, alongside the benefits, there has been an alarming rise in hacking gadgets that pose serious threats to personal security and privacy. These devices range from simple tools that can intercept
December 23, 2024By Prapattimynk
Introduction to Hacking Gadgets In the modern digital landscape, hacking gadgets represent a unique category of devices that are often associated with cybercrime and unauthorized access to computer systems. These gadgets can range from sophisticated hardware tools designed to exploit vulnerabilities in networks to simple devices that can be used to bypass security measures. While
December 16, 2024By Prapattimynk
Install Or download from releases after installation run cent init to initialize cent with the configuration files you find here Supported commands Command Description check Check if templates repo are still available init Cent init configuration file summary Print summary table update Update your repository validate Validate templates, if the template is invalid it is
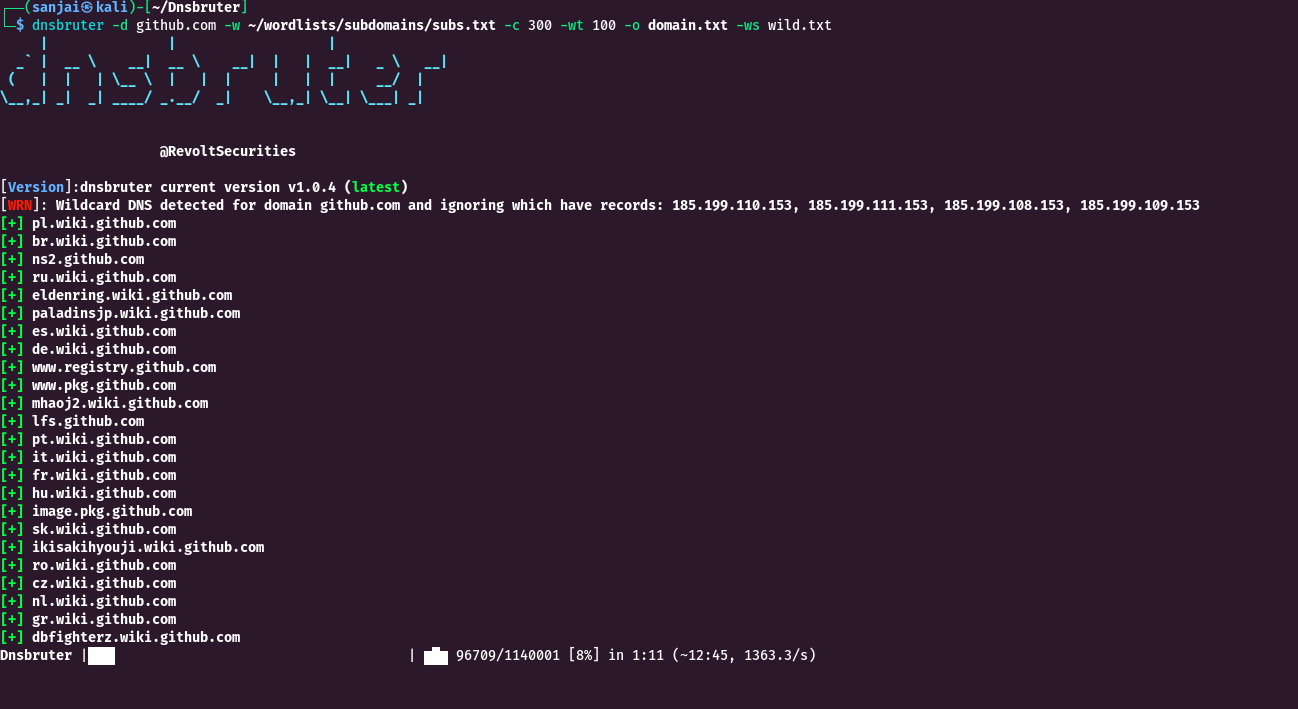
December 16, 2024By Prapattimynk
Improved Speed & Efficiency: Significantly faster and smoother DNS brute-forcing with lightweight resource usage. Memory & Resource Management: Optimized to handle large-scale DNS scans without consuming excessive system resources. Flexible Input: Supports both stdin and file-based domain lists for DNS brute-forcing. Concurrency Control: Rate limiting and concurrency management to ensure stable performance under heavy loads.
June 26, 2024By Prapattimynk
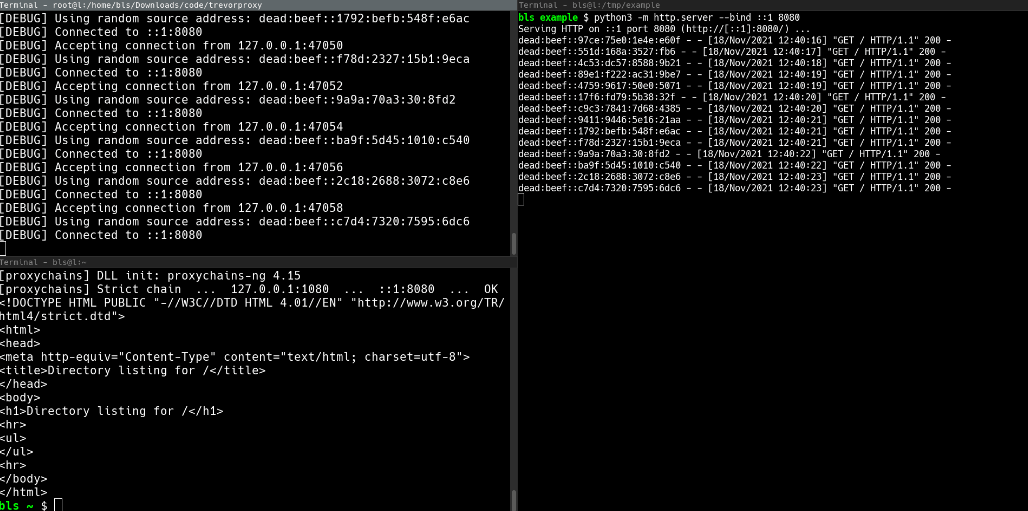
Installation pip install git+https://github.com/blacklanternsecurity/trevorproxy See the accompanying Blog Post for a fun rant and some cool demos! A SOCKS proxy written in Python that randomizes your source IP address. Round-robin your evil packets through SSH tunnels or give them billions of unique source addresses! TREVORproxy IPv6 Subnet Proxy Diagram TREVORproxy SSH Proxy Demo TREVORproxy Subnet
June 26, 2024By Prapattimynk
A program to dub multi-lingual media and anime using modern AI speech synthesis, diarization, language identification, and voice cloning. Download Release 1.0 You can try the first binary version which has access to basic dubbing features with the non-AI based libraries for Windows and Linux. This is a good way to try out the program