January 14, 2024By Prapattimynk
This repository contains an advanced Bash script designed for conducting digital forensics on Linux systems. The script automates the collection of a wide range of system and user data, making it a valuable tool for IT professionals, system administrators, and digital forensic investigators. https://github.com/vm32/Digital-Forensics-Script-for-Linux Features Usage Requirements Security and Privacy Linux Distribution Compatibility The advanced
January 14, 2024By Prapattimynk
PyWebCopy is a free tool for copying full or partial websites locally onto your hard-disk for offline viewing. https://github.com/rajatomar788/pywebcopy/ PyWebCopy will scan the specified website and download its content onto your hard-disk. Links to resources such as style-sheets, images, and other pages in the website will automatically be remapped to match the local path. Using
January 14, 2024By Prapattimynk
https://github.com/openrewrite/rewrite The OpenRewrite project is a mass source code refactoring ecosystem. Reduce 1000s of hours of static code analysis fixes to minutes. Turn a four-month migration project into four hours of work. Patch security vulnerabilities across 100s of repositories at once. OpenRewrite automates code refactoring and remediation tasks for you, enabling developers to deliver more
January 14, 2024By Prapattimynk
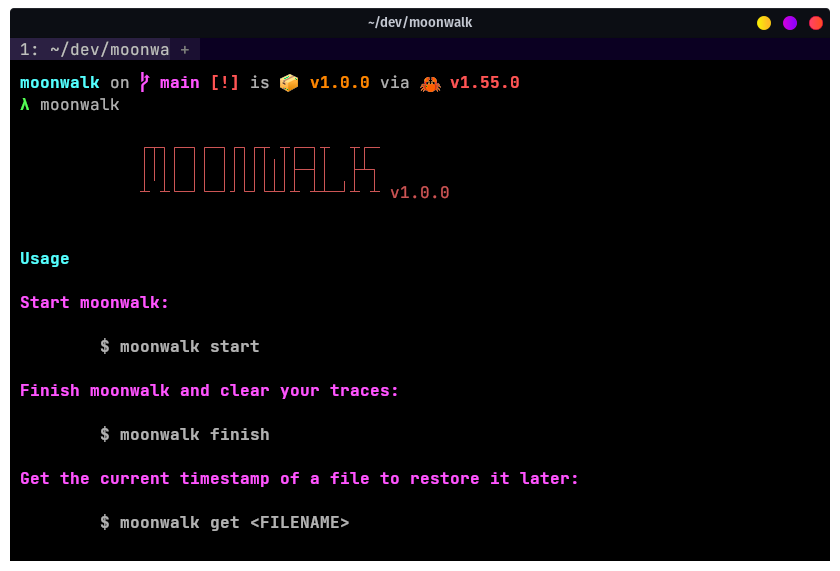
https://github.com/Aditya-dom/moonwalk-back Cover your tracks during Linux Exploitation by leaving zero traces on system logs and filesystem timestamps. moonwalk-back is a 400 KB single-binary executable that can clear your traces while penetration testing a Unix machine. It saves the state of system logs pre-exploitation and reverts that state including the filesystem timestamps post-exploitation leaving zero traces of a ghost in
January 14, 2024By Prapattimynk
https://github.com/cryptpad/cryptpad CryptPad is a collaboration suite that is end-to-end-encrypted and open-source. It is built to enable collaboration, synchronizing changes to documents in real time. Because all data is encrypted, the service and its administrators have no way of seeing the content being edited and stored. CryptPad offers a variety of collaborative tools that encrypt your
January 14, 2024By Prapattimynk
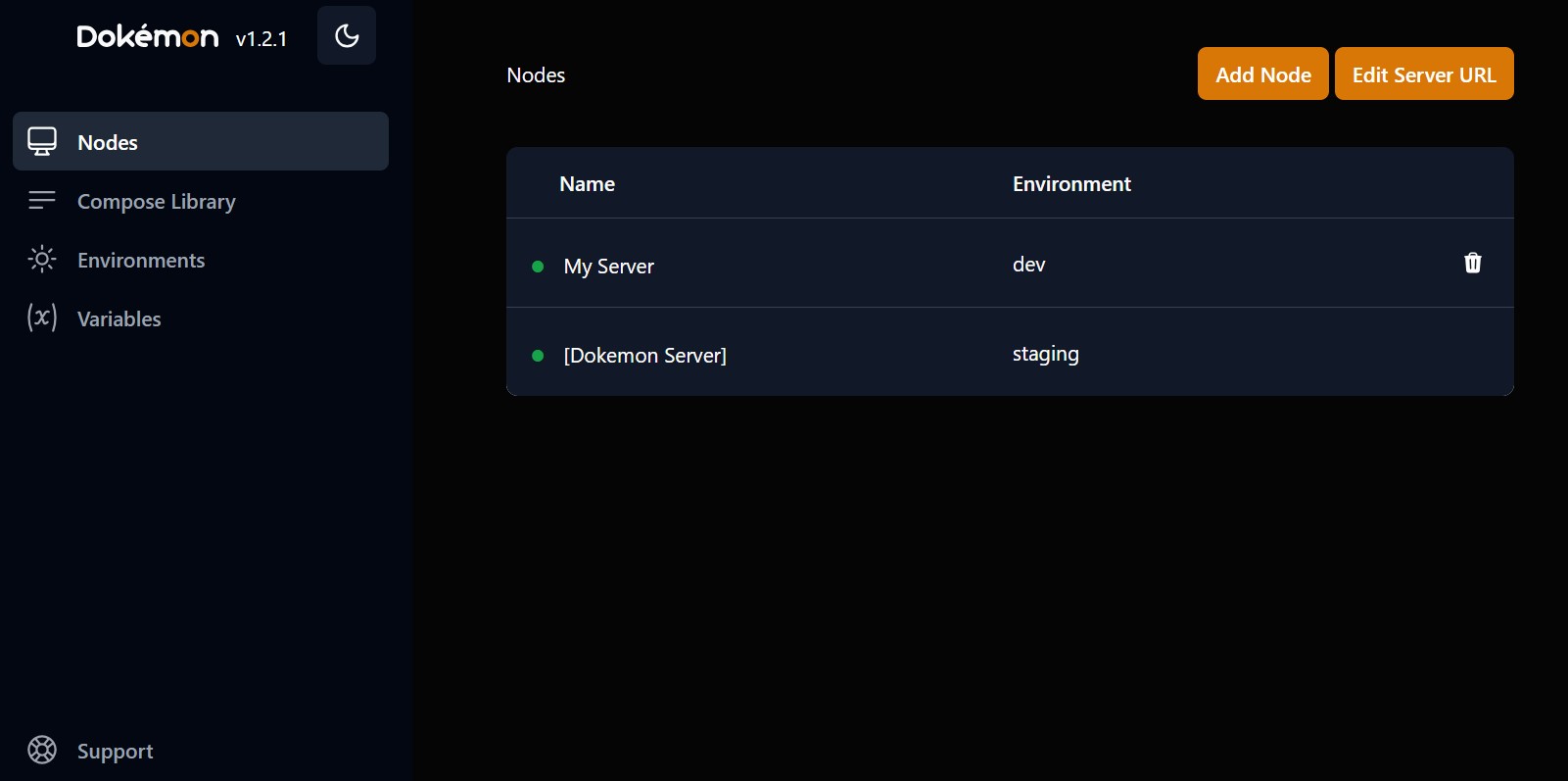
https://github.com/productiveops/dokemon Dokémon is a friendly GUI for managing Docker Containers. You can manage multiple servers from a single Dokemon instance. Check https://dokemon.dev for more details. Production Usage We recommend that you run Dokemon on a private network whenever possible. If you are running on a VPS with only public access, we recommend that you use an SSL
November 16, 2023By Prapattimynk
For the purposes of this article, I would like to distinguish two topics: Vulnerability Details describing single security issue raised as a part of bigger report or bug bounty activities; A Formal Vulnerability Report is created as a result of security assessments and may contain more than one vulnerability. Vulnerability details describes single security issue or
August 1, 2023By Prapattimynk
Welcome to the comprehensive guide on “How to Hack an Instagram Account” designed specifically for beginners. In this blog , we gonna talk about instagram , facebook and whatsapp hacking in detail because this topic is very popular between beginners . Before we proceed, it’s essential to clarify that hacking into someone’s account without their
July 25, 2023By Prapattimynk
SQLmap is a powerful open-source penetration testing tool used to detect and exploit SQL injection vulnerabilities in web applications. It provides a comprehensive set of features that assist both security professionals and beginners in identifying and assessing database vulnerabilities. In this blog post, we will delve into the world of SQLmap and provide a step-by-step
June 30, 2023By Prapattimynk
Programming languages serve as the foundation for developing software applications, but they are not immune to security vulnerabilities. In this article, we will explore the various security issues that can arise in programming languages, ranging from poor input validation to code injection attacks. By understanding these issues, developers can take proactive measures to enhance the
June 26, 2023By Prapattimynk
Introduction In today’s digital age, our smartphones have become an integral part of our lives. We use them for communication, accessing personal and financial information, and staying connected with the world. However, this increased reliance on mobile devices also raises concerns about security. The question “Is my phone hacked?” is one that many individuals ask,
June 25, 2023By Prapattimynk
Introduction In the world of cybersecurity, vulnerability refers to weaknesses or flaws in systems that can be exploited by malicious actors to gain unauthorized access or cause harm. While vulnerabilities can exist in various contexts, there are situations where the presence of differential vulnerability becomes a significant factor. This article explores examples of such situations
June 16, 2023By Prapattimynk
Introduction: In the realm of cybersecurity, parameter tampering stands as a potent technique used by both ethical hackers and malicious actors to exploit vulnerabilities in web applications. One such nefarious application of parameter tampering is price tempering, wherein hackers manipulate input parameters to modify product prices or alter transaction values. This article explores the concept
June 13, 2023By Prapattimynk
The .htaccess file is a powerful configuration file utilized by web servers, particularly Apache, to control and modify various aspects of website behavior. While primarily designed for enhancing security and performance, the .htaccess file can also become a weapon in the hands of skilled attackers. In this article, we will delve into the realm of
June 11, 2023By Prapattimynk
Remote Code Execution (RCE) is a security vulnerability that allows an attacker to execute arbitrary code remotely on a targeted system. It can have severe consequences, enabling attackers to take complete control over the compromised system. This tutorial will guide you through understanding RCE, how to find it, and provide some code examples for better
June 10, 2023By Prapattimynk
Introduction HTTP flooding, also known as HTTP DoS (Denial of Service), is a type of cyber attack where an attacker overwhelms a target website or server by flooding it with a massive number of HTTP requests. The goal of this attack is to exhaust the server’s resources, such as bandwidth, processing power, or memory, causing
- 1
- 2
Guide
APKDeepLens artificial-intelligence AttackGEn Audit BIBT BITB bluetooth Burpsuite Bypass EDR Captcha Solver Clone Websites Digital Forensics Draw2Img error-based SQL injection Extension File Transfer Flying Carpet HTML Smuggling Incident Response Testing Information Gathering installation process Labs Linux Maltrail networking Network security Network Traversal Nuclei AI Osint PDF Tool Pentesting Tool PiAlert Piper privilege escalation puter pyWebCopy QR File Share SQL injection Stirling-PDF System logs Text To Voice Threat Tool Toolkit Voice Clone