April 27, 2024By Prapattimynk
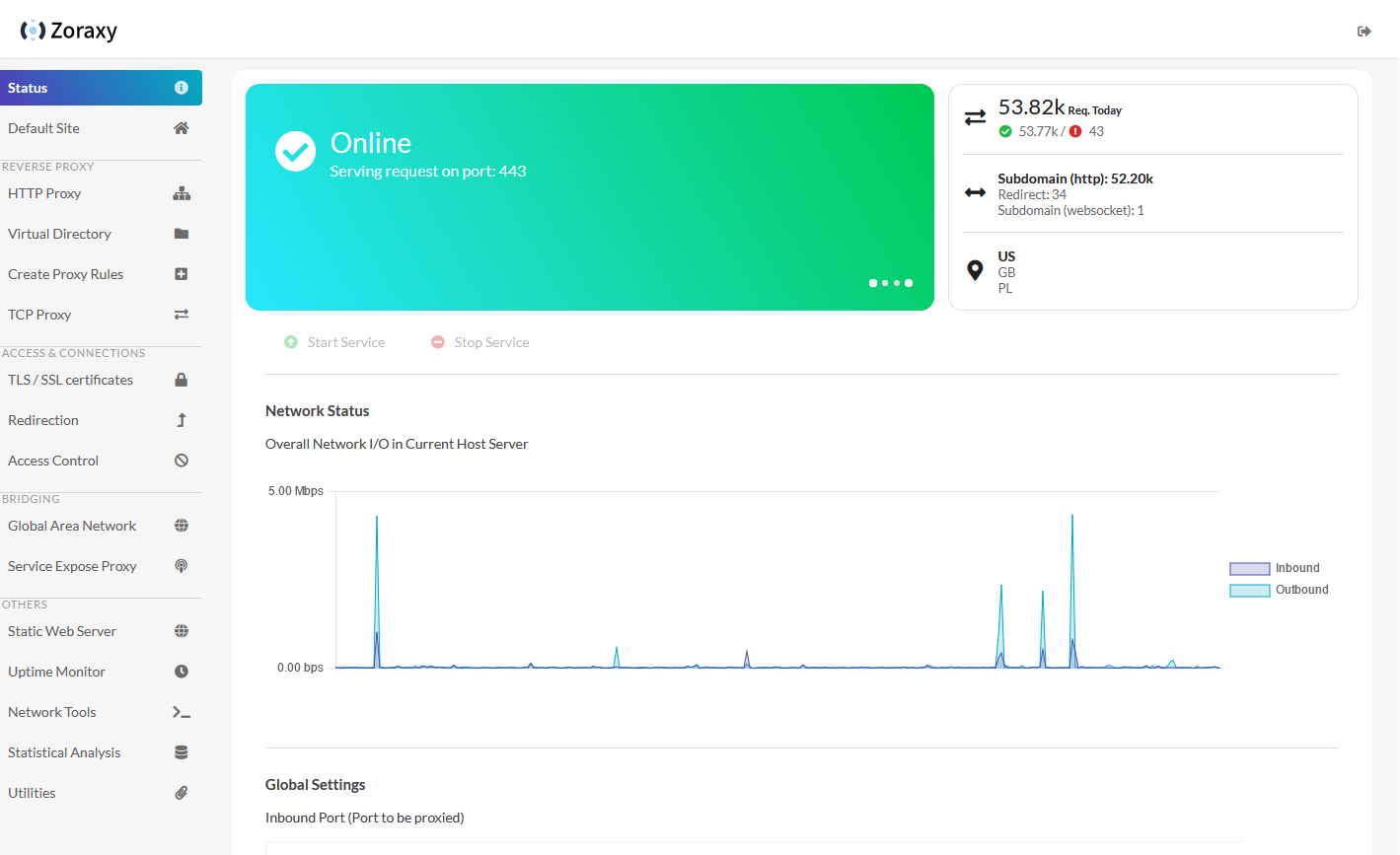
https://github.com/tobychui/zoraxy General purpose request (reverse) proxy and forwarding tool for networking noobs. Now written in Go! Zoraxy v3 HTTP proxy config is not compatible with the older v2. If you are looking for the legacy version of Zoraxy, take a look at the v2 branch Features Downloads Windows /Linux (amd64) /Linux (arm64) For other systems or architectures, please
April 4, 2024By Prapattimynk
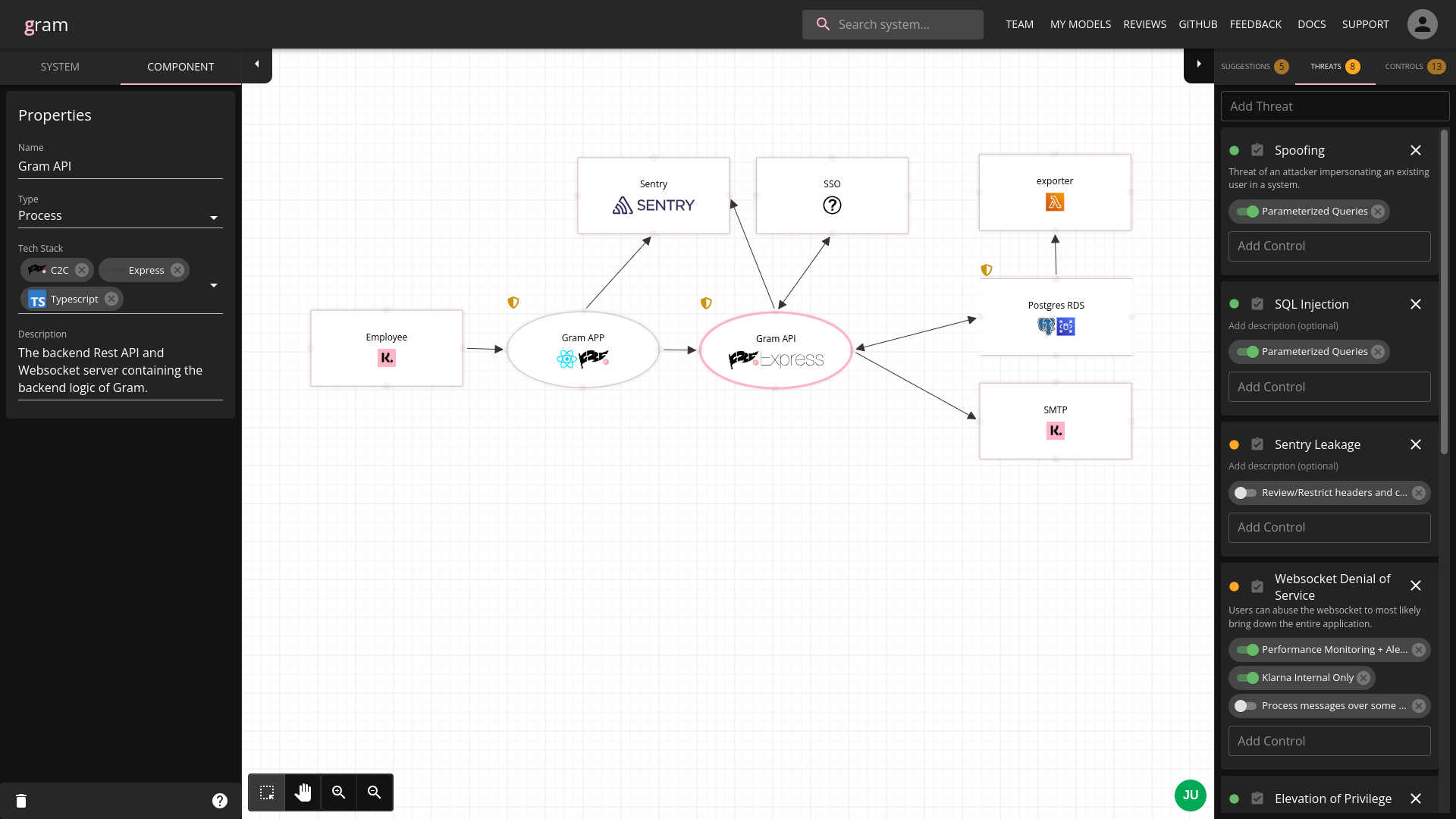
https://github.com/klarna-incubator/gram Gram is Klarna’s own threat model diagramming tool developed internally by Klarna’s Secure Development team. It is a webapp for engineers to collaboratively create threat models for their systems, providing a easy-to-understand way to document a system as a dataflow diagram with threats/controls attached. Features ✨ Getting Started 🚀 See Quick Start.
March 26, 2024By Prapattimynk
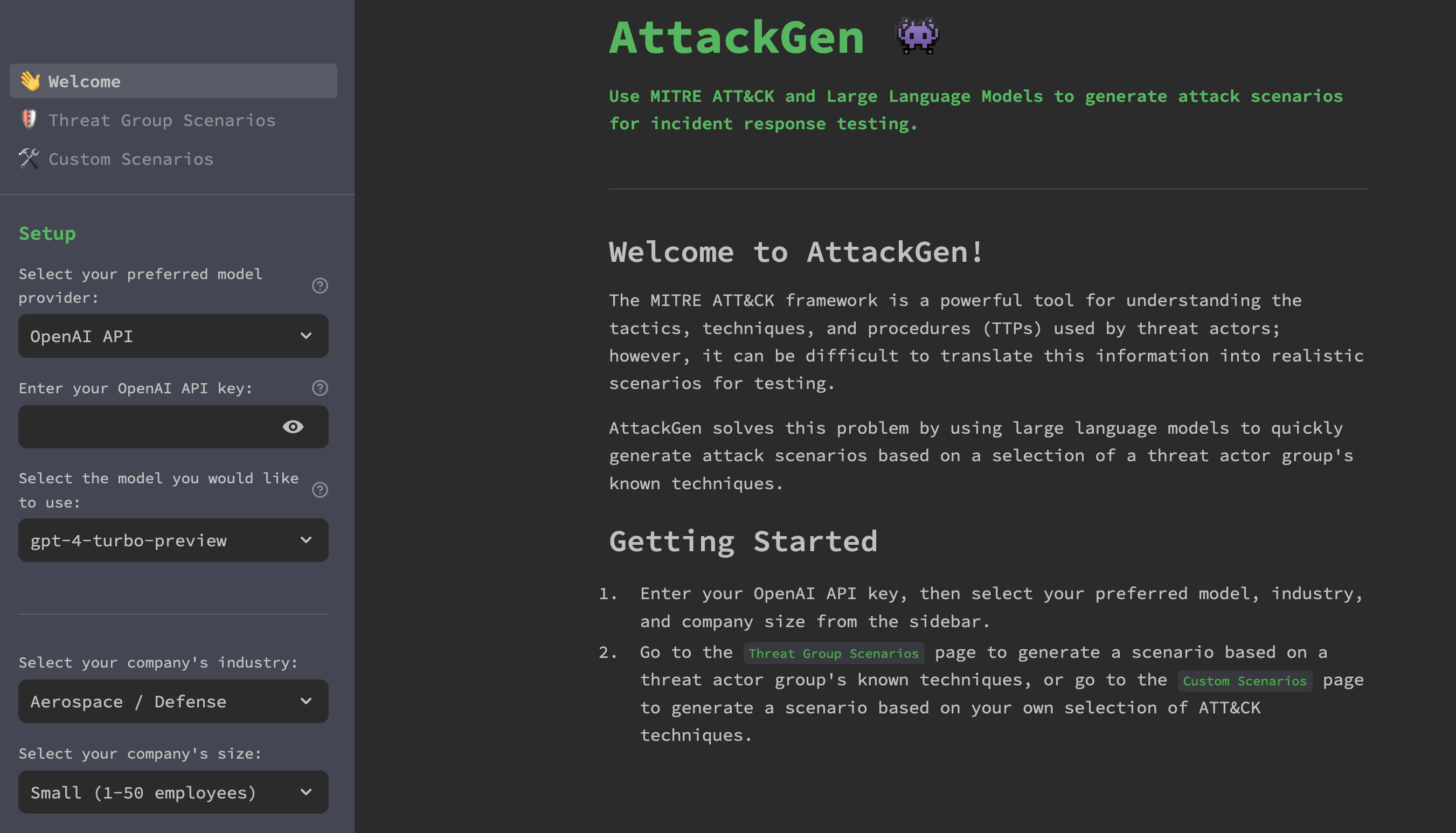
https://github.com/mrwadams/attackgen AttackGen is a cybersecurity incident response testing tool that leverages the power of large language models and the comprehensive MITRE ATT&CK framework. The tool generates tailored incident response scenarios based on user-selected threat actor groups and your organisation’s details. Features Requirements Installation Option 1: Cloning the Repository Option 2: Using Docker LangSmith Setup If
March 23, 2024By Prapattimynk
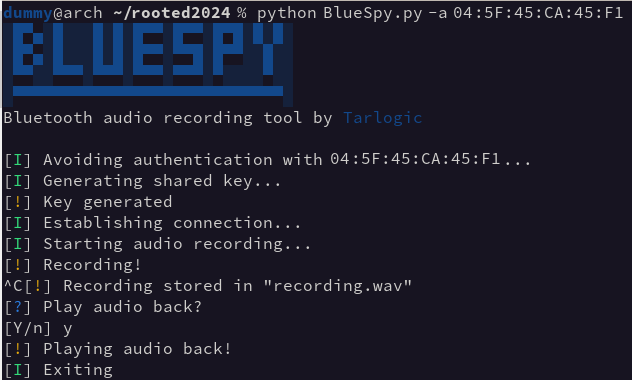
https://github.com/TarlogicSecurity/BlueSpy This repository contains the implementation of a proof of concept to record and replay audio from a bluetooth device without the legitimate user’s awareness. The PoC was demonstrated during the talk BSAM: Seguridad en Bluetooth at RootedCON 2024 in Madrid. It’s designed to raise awareness about the insecure use of Bluetooth devices, and the need of a consistent
January 30, 2024By Prapattimynk
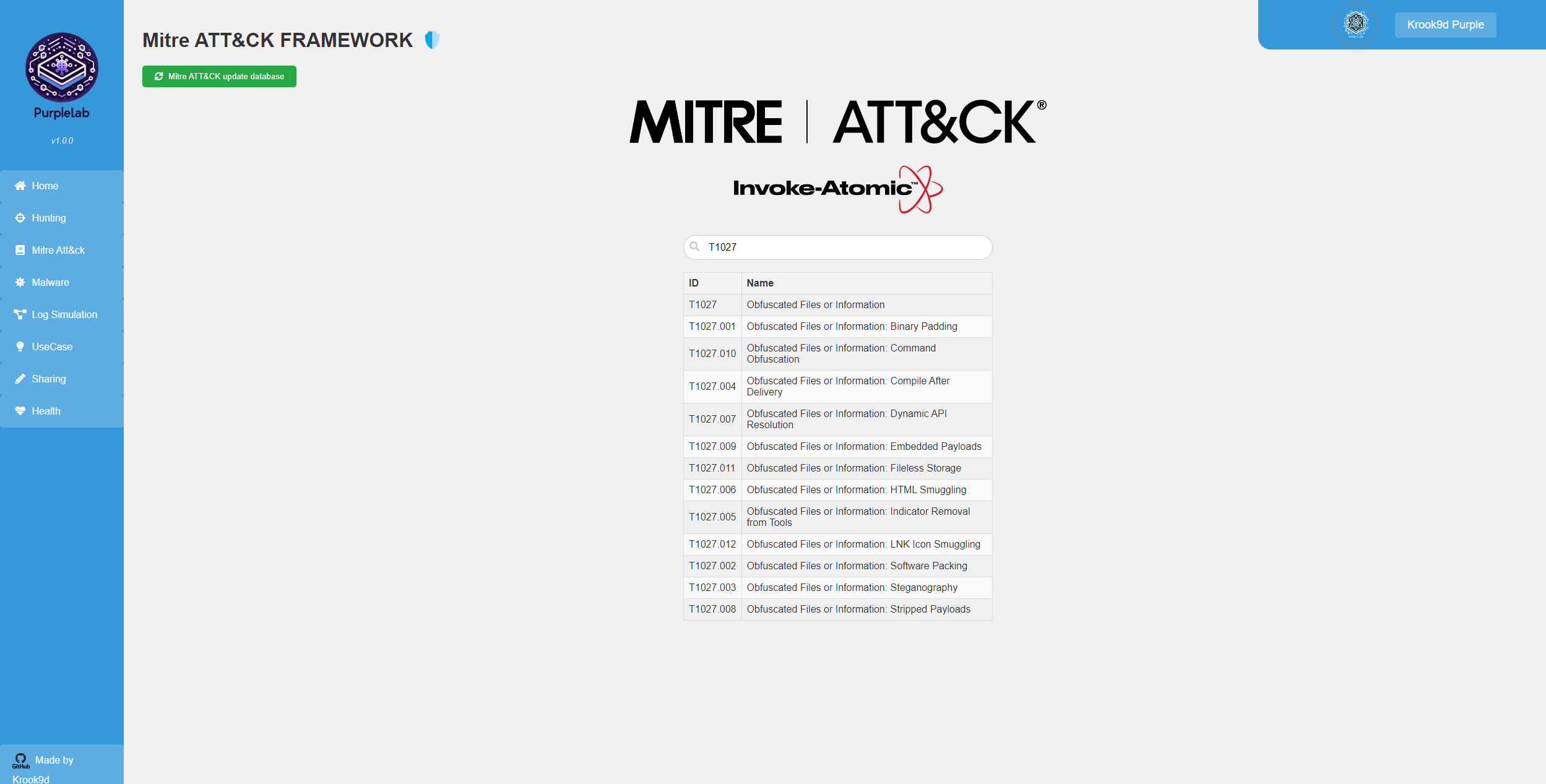
What is PurpleLab ? This solution will allow you to easily deploy an entire lab to create/test your detection rules, simulate logs, play tests, download and run malware and mitre attack techniques, restore the sandbox and many other features. https://github.com/Krook9d/PurpleLab The lab contains : Installation procedure ⚠️ To have a fully clean installation, you have to
January 28, 2024By Prapattimynk
https://github.com/spieglt/FlyingCarpet Send and receive files between Android, iOS, Linux, macOS, and Windows over ad hoc WiFi. No shared network or cell connection required, just two devices with WiFi chips in close range. Don’t have a flash drive? Don’t have access to a wireless network? Need to move a file larger than 2GB between different filesystems
January 14, 2024By Prapattimynk
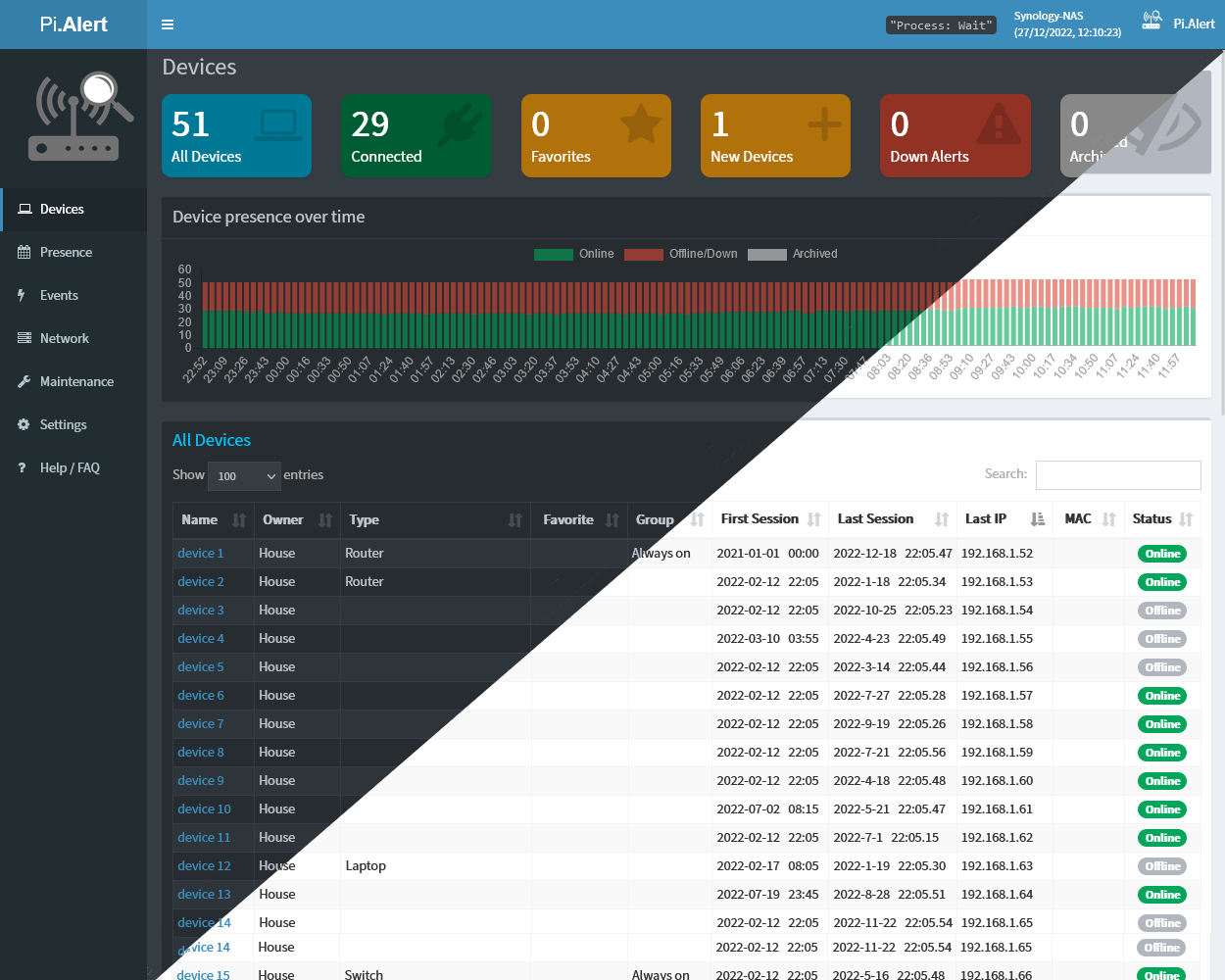
Get visibility of what’s going on on your WIFI/LAN network. Scan for devices, port changes and get alerts if unknown devices or changes are found. Write your own Plugins with auto-generated UI and in-build notification system. https://github.com/jokob-sk/Pi.Alert Why PiAlert❓ Most of us don’t know what’s going on on our home network, but we want our
January 14, 2024By Prapattimynk
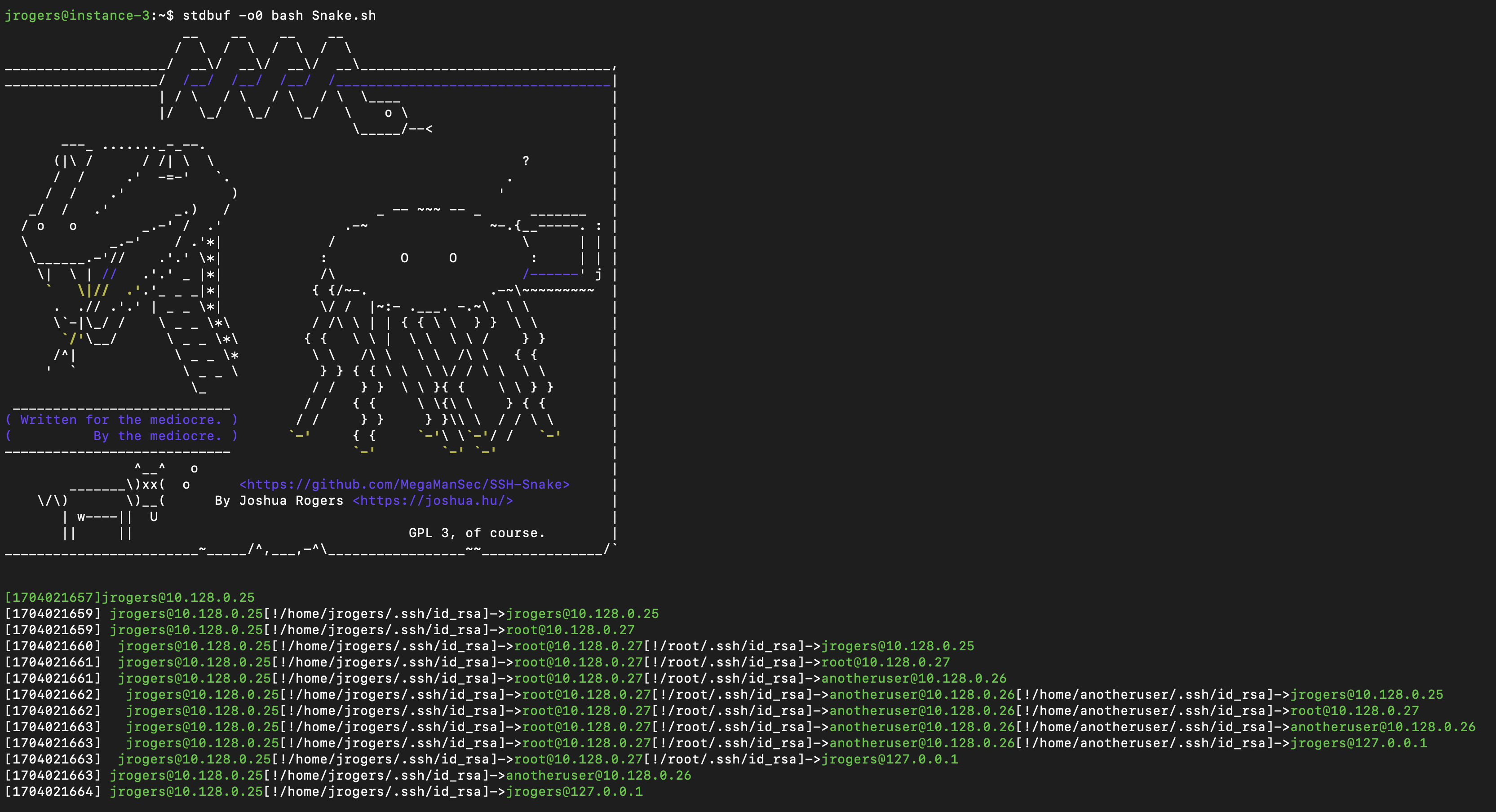
https://github.com/MegaManSec/SSH-Snake SSH-Snake is a powerful tool designed to perform automatic network traversal using SSH private keys discovered on systems, with the objective of creating a comprehensive map of a network and its dependencies to identify the extent that a network can be compromised using SSH and SSH private keys starting from a particular system. SSH-Snake
January 14, 2024By Prapattimynk
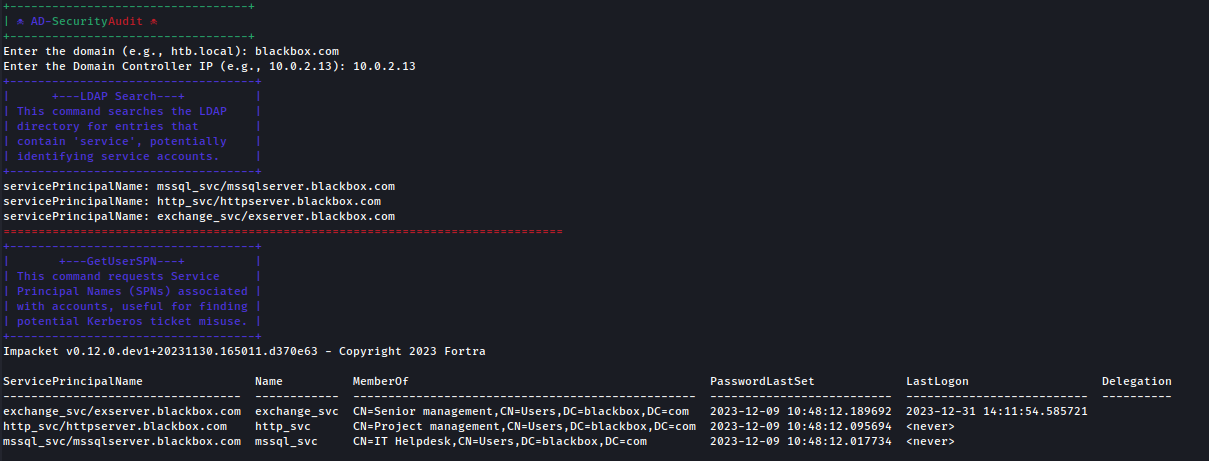
https://github.com/emrekybs/AD-AssessmentKit Contains a collection of Bash scripts designed for comprehensive security audits and network mapping of Active Directory (AD) environments. The scripts automate various tasks including LDAP querying, Kerberos ticket analysis, SMB enumeration, and exploitation of known vulnerabilities like Zerologon and PetitPotam. AD-SecurityAudit.sh Focuses on initial reconnaissance and vulnerability identification in AD domains, requiring only
January 14, 2024By Prapattimynk
https://github.com/cryptpad/cryptpad CryptPad is a collaboration suite that is end-to-end-encrypted and open-source. It is built to enable collaboration, synchronizing changes to documents in real time. Because all data is encrypted, the service and its administrators have no way of seeing the content being edited and stored. CryptPad offers a variety of collaborative tools that encrypt your
January 14, 2024By Prapattimynk
https://github.com/productiveops/dokemon Dokémon is a friendly GUI for managing Docker Containers. You can manage multiple servers from a single Dokemon instance. Check https://dokemon.dev for more details. Production Usage We recommend that you run Dokemon on a private network whenever possible. If you are running on a VPS with only public access, we recommend that you use an SSL
January 14, 2024By Prapattimynk
https://github.com/akamai/ddspoof DDSpoof is a tool that enables DHCP DNS Dynamic Update attacks against Microsoft DHCP servers in AD environments. For additional information, please refer to our blog posts: For information on how to mitigate DDSpoofing attacks in your networks, please refer to Invoke-DHCPCheckup.ps1 Setup Usage Commandline arguments: At startup, DDSpoof will perform the following: After the
June 13, 2023By Prapattimynk
The .htaccess file is a powerful configuration file utilized by web servers, particularly Apache, to control and modify various aspects of website behavior. While primarily designed for enhancing security and performance, the .htaccess file can also become a weapon in the hands of skilled attackers. In this article, we will delve into the realm of
June 10, 2023By Prapattimynk
Introduction HTTP flooding, also known as HTTP DoS (Denial of Service), is a type of cyber attack where an attacker overwhelms a target website or server by flooding it with a massive number of HTTP requests. The goal of this attack is to exhaust the server’s resources, such as bandwidth, processing power, or memory, causing
June 6, 2023By Prapattimynk
Discover the ultimate comprehensive guide for beginners on DDoS attacks. Dive into the realms of network security, botnets, packet floods, network intrusion, UDP flooding, HTTP flooding, SYN flood, prevention techniques, and vital safety measures. Equip yourself with knowledge and practical insights to defend against these cyber threats and safeguard your digital infrastructure effectively. What is
Network security
APKDeepLens artificial-intelligence AttackGEn Audit BIBT BITB bluetooth Burpsuite Bypass EDR Captcha Solver Clone Websites Digital Forensics Draw2Img error-based SQL injection Extension File Transfer Flying Carpet HTML Smuggling Incident Response Testing Information Gathering installation process Labs Linux Maltrail networking Network security Network Traversal Nuclei AI Osint PDF Tool Pentesting Tool PiAlert Piper privilege escalation puter pyWebCopy QR File Share SQL injection Stirling-PDF System logs Text To Voice Threat Tool Toolkit Voice Clone