Most web application firewalls (WAFs) have limitations for how much data they can process when a request body is sent. This means for HTTP requests that contain a request body (i.e. POST, PUT, PATCH etc), it is usually possible to bypass the WAF by simply prepending junk data.
When the request is padded with this junk data, the WAF will process up to X kb of the request and analyze it, but everything after the limits of the WAF will pass straight through.
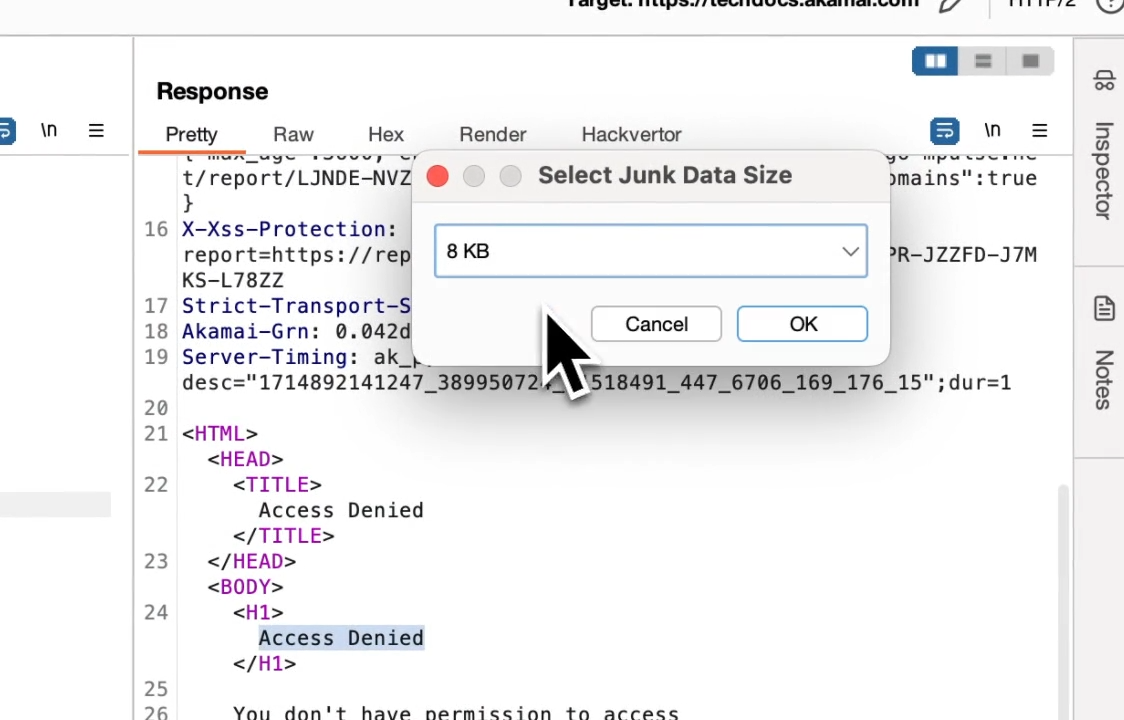
nowafpls is a simple Burp plugin which will contextually insert this junk data into your HTTP request inside the repeater tab. You can select from a preset amount of junk data you want inserted, or you can insert an arbitrary amount of junk data by selecting the “Custom” option.
This tool is just 80 or so lines of Python, it’s incredibly simple but works for most WAFs lol.
Documented WAF Limitations
| WAF Provider | Maximum Request Body Inspection Size Limit |
|---|---|
| Cloudflare | 128 KB for ruleset engine, up to 500 MB for enterprise |
| AWS WAF | 8 KB – 64 KB (configurable depending on service) |
| Akamai | 8 KB – 128 KB |
| Azure WAF | 128 KB |
| Fortiweb by Fortinet | 100 MB |
| Barracuda WAF | 64 KB |
| Sucuri | 10 MB |
| Radware AppWall | up to 1 GB for cloud WAF |
| F5 BIG-IP WAAP | 20 MB (configurable) |
| Palo Alto | 10 MB |
| Cloud Armor by Google | 8 KB (can be increased to 128 KB) |
Installing nowafpls
nowafpls is a Jython based Burp Plugin.
- Clone or download this repo.
- Go to the extensions tab in Burp Suite.
- Click “Add”
- Select Extension Type – Python
- Select “nowafpls.py” that you downloaded in Step 1
Using nowafpls
https://github.com/assetnote/nowafpls/assets/5241936/dad77c3a-d550-4e5d-894d-027256137148
- Send any request to the repeater tab that you’d like to bypass WAF for.
- Put your cursor in a place you would like to insert junk data.
- Right click -> Extensions -> nowafpls
- Select how much junk data you want to insert
- Click “OK”
nowafpls will insert junk data as per the type of request (URLEncoded/XML/JSON) automatically.
Caido Version
The Caido version of this plugin is maintained by @Rhynorater and can be found at the below gist:
https://gist.github.com/Rhynorater/ace68d4976357ca0937cb4669f303306or in the EvenBetter Workflow Library.
Authors
- Shubham Shah – Initial work – github
License
MIT


What do you think?
Show comments / Leave a comment