The ARP protocol relies on mapping IP addresses to MAC addresses. In an ARP spoofing attack, an attacker sends fake ARP messages to devices on the network, claiming to have the MAC address of another device (such as a router or another computer). This misleads other devices, so their data traffic is sent to the attacker instead of the intended target.
❓ How the attack works in detail:
1️⃣ Attacker on the network: The attacker must be connected to the same local area network (LAN) as the victims.
2️⃣ Sending fake ARP messages: The attacker sends fake ARP ” replies ” messages to the targeted devices, these messages falsely announce that the attacker’s MAC address is associated with the IP address of another device (such as a router).
3️⃣ ARP Table Update: Targeted devices receive these fake messages and update their ARP tables with false information, now linking the router’s IP address to the attacker’s MAC address.
4️⃣ Traffic Interception: Now when any targeted device tries to send data to the router (or any other targeted device), the data is actually sent to the attacker.
✅ Attacker Options:
🟢 Data interception only: An attacker can simply intercept and read data without the victims noticing anything.
🟢 Data modification: An attacker can modify data before it is resent to its destination.
🟢 Data Denial: An attacker can completely prevent data from reaching its destination, causing victims to lose connectivity.
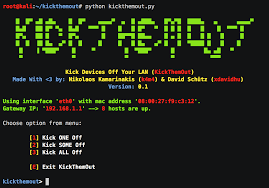
⚙️ KickThemOut Tool:
KickThemOut is a simple tool used to perform ARP spoofing attacks with the aim of disconnecting devices from the network.
🔥 Simplified practical example (for educational purposes only):
Note : This example assumes you are running the test on a network that you own or have explicit permission to run tests on.
✔️ Requirements:
🟢 A computer running Linux (preferably Kali Linux or any other penetration testing distribution).
🟢 KickThemOut tool installed.
✅ Steps:
1️⃣ Identify the IP address of the victim and the router: Use a tool like netdiscover or nmap to find the IP addresses of the devices on the network.
2️⃣ Run KickThemOut: Open a terminal window and type the following command (replacing [victim’s IP address] with the victim’s actual IP address):
sudo kickthemout -i [network interface] [victim’s IP address]
⏺ [ Network interface] :: This is the network interface you are using (such as wlan0 or eth0), you can find out the network interface using the ip a command.
⏺ For example: sudo kickthemout -i wlan0 192.168.1.10 (http://192.168.1.10/)
⏺ Monitor the results: The tool will start sending fake ARP messages to the victim, which will disconnect them from the network.


What do you think?
Show comments / Leave a comment