June 16, 2024By Prapattimynk
What is keyFinder? keyFinder is chrome extension that searches the DOM for any embedded script link, as script tag may contain keys for specific API(such as Google maps API) and you can add keywords to search for it at any website you visit. Features: it searches the DOM for “src” of scripts and see if
June 14, 2024By Prapattimynk
Crawl4AI v0.2.3 🕷️🤖 Crawl4AI has one clear task: to simplify crawling and extract useful information from web pages, making it accessible for large language models (LLMs) and AI applications. 🆓🌐 Use as REST API: Check Use as Python library: Recent Changes v0.2.3 🎨 Extract and return all media tags (Images, Audio, and Video). Check result.media
June 14, 2024By Prapattimynk
IconJector This is a Windows Explorer DLL injection technique that uses the change icon dialog on Windows. https://github.com/0xda568/IconJector/assets/61665703/bbf53775-ad8d-422b-b186-663ff5074976 How does it work? Firstly, a folder is created in the temp directory, and the properties of the folder are opened using SHObjectProperties. To retrieve the handle of the window independently of the system language, EnumWindows is
June 14, 2024By Prapattimynk
Project that generates Malicious Office Macro Enabled Dropper for DLL SideLoading and Embed it in Lnk file to bypass MOTW Install requirements pip install -r requirements.txt Video Demonstration https://github.com/SaadAhla/dropper/assets/123980007/7db05d2c-05e5-4a70-b967-6faecd7a296e Direct View On Github
April 27, 2024By Prapattimynk
https://github.com/tobychui/zoraxy General purpose request (reverse) proxy and forwarding tool for networking noobs. Now written in Go! Zoraxy v3 HTTP proxy config is not compatible with the older v2. If you are looking for the legacy version of Zoraxy, take a look at the v2 branch Features Downloads Windows /Linux (amd64) /Linux (arm64) For other systems or architectures, please
April 4, 2024By Prapattimynk
https://github.com/klarna-incubator/gram Gram is Klarna’s own threat model diagramming tool developed internally by Klarna’s Secure Development team. It is a webapp for engineers to collaboratively create threat models for their systems, providing a easy-to-understand way to document a system as a dataflow diagram with threats/controls attached. Features ✨ Getting Started 🚀 See Quick Start.
March 26, 2024By Prapattimynk
https://github.com/mrwadams/attackgen AttackGen is a cybersecurity incident response testing tool that leverages the power of large language models and the comprehensive MITRE ATT&CK framework. The tool generates tailored incident response scenarios based on user-selected threat actor groups and your organisation’s details. Features Requirements Installation Option 1: Cloning the Repository Option 2: Using Docker LangSmith Setup If
March 23, 2024By Prapattimynk
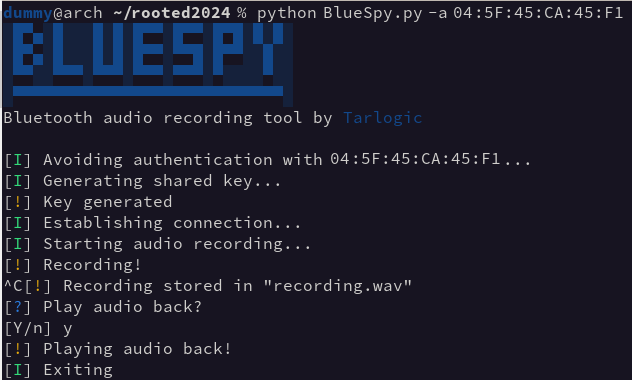
https://github.com/TarlogicSecurity/BlueSpy This repository contains the implementation of a proof of concept to record and replay audio from a bluetooth device without the legitimate user’s awareness. The PoC was demonstrated during the talk BSAM: Seguridad en Bluetooth at RootedCON 2024 in Madrid. It’s designed to raise awareness about the insecure use of Bluetooth devices, and the need of a consistent
March 11, 2024By Prapattimynk
https://github.com/d78ui98/APKDeepLens APKDeepLens is a Python based tool designed to scan Android applications (APK files) for security vulnerabilities. It specifically targets the OWASP Top 10 mobile vulnerabilities, providing an easy and efficient way for developers, penetration testers, and security researchers to assess the security posture of Android apps. Features APKDeepLens is a Python-based tool that performs
January 30, 2024By Prapattimynk
What is PurpleLab ? This solution will allow you to easily deploy an entire lab to create/test your detection rules, simulate logs, play tests, download and run malware and mitre attack techniques, restore the sandbox and many other features. https://github.com/Krook9d/PurpleLab The lab contains : Installation procedure ⚠️ To have a fully clean installation, you have to
January 20, 2024By Prapattimynk
Freeze.rs is a payload creation tool used for circumventing EDR security controls to execute shellcode in a stealthy manner. Freeze.rs utilizes multiple techniques to not only remove Userland EDR hooks, but to also execute shellcode in such a way that it circumvents other endpoint monitoring controls. https://github.com/Tylous/Freeze.rs Creating A Suspended Process When a process is
January 15, 2024By Prapattimynk
https://github.com/TheCyb3rAlpha/BobTheSmuggler “Bob the Smuggler”: A tool that leverages HTML Smuggling Attack and allows you to create HTML files with embedded 7z/zip archives. The tool would compress your binary (EXE/DLL) into 7z/zip file format, then XOR encrypt the archive and then hides inside PNG/GIF image file format (Image Polyglots). Quick Update Jan 15th, 2024 – Support for
January 14, 2024By Prapattimynk
Get visibility of what’s going on on your WIFI/LAN network. Scan for devices, port changes and get alerts if unknown devices or changes are found. Write your own Plugins with auto-generated UI and in-build notification system. https://github.com/jokob-sk/Pi.Alert Why PiAlert❓ Most of us don’t know what’s going on on our home network, but we want our
January 14, 2024By Prapattimynk
This repository contains an advanced Bash script designed for conducting digital forensics on Linux systems. The script automates the collection of a wide range of system and user data, making it a valuable tool for IT professionals, system administrators, and digital forensic investigators. https://github.com/vm32/Digital-Forensics-Script-for-Linux Features Usage Requirements Security and Privacy Linux Distribution Compatibility The advanced
January 14, 2024By Prapattimynk
https://github.com/MegaManSec/SSH-Snake SSH-Snake is a powerful tool designed to perform automatic network traversal using SSH private keys discovered on systems, with the objective of creating a comprehensive map of a network and its dependencies to identify the extent that a network can be compromised using SSH and SSH private keys starting from a particular system. SSH-Snake
January 14, 2024By Prapattimynk
https://github.com/BeichenDream/GodPotato Based on the history of Potato privilege escalation for 6 years, from the beginning of RottenPotato to the end of JuicyPotatoNG, I discovered a new technology by researching DCOM, which enables privilege escalation in Windows 2012 – Windows 2022, now as long as you have “ImpersonatePrivilege” permission. Then you are “NT AUTHORITY\SYSTEM”, usually WEB