What is PurpleLab ?
This solution will allow you to easily deploy an entire lab to create/test your detection rules, simulate logs, play tests, download and run malware and mitre attack techniques, restore the sandbox and many other features.
https://github.com/Krook9d/PurpleLab
The lab contains :
- A web interface with a complete front end to control features
- The Virtualbox tool with a ready-to-use Windows 10 VM
- A Flask back end
- A mysql database
- A pfsense (coming soon)
- A linux VM (coming soon)
Installation procedure
⚠️ To have a fully clean installation, you have to follow all the chapiter of the installation procedure from requirements to account
⚠️ NOTE: This lab has not been hardened in any way and runs with basic credentials. Please do not connect or bridge it to any networks you care about, or secure it yourself with a PKI, better authentication systems, etc.
Requirements
Minimum Hardware resources :
- 2 processors
- 13GB RAM
A clean installation of Ubuntu server 22.04 available : Here
⚠️ If you use Ubuntu server 23.10 you will have issues with python library installation
⚠️ Enable Hardware Virtualization ⚠️ :
In VM Ware workstation -> Go to the settings of the VM -> Processors -> Virtualization engine -> enable “Virtualize Intel VT-x/EPT or AMD-V/RVI” In Virtualbox -> In physical machine -> Set your mother board to allow Hardware Virtualization
In your home folder, Download repo :git clone https://github.com/Krook9d/PurpleLab.git
Preparing files :mv PurpleLab/install.sh .
installation
run :sudo bash install.sh
ELK Configuration
- In the admin.txt file on your home directory, copy the enrolment token The token is located below the line “he generated password for the elastic built-in superuser is”. Then go to the “Hunting” page to open ELK and copy it when prompted.
- After pasting the enrolment token, you’ll be asked for a verification code. Here’s how to obtain it
sudo /usr/share/kibana/bin/kibana-verification-code
Note: To regenerate the token you can use this command :
/usr/share/elasticsearch/bin/elasticsearch-create-enrollment-token --scope kibana
If you have issues submitting the enrolment token restart the elastic search serviceservice elasticsearch restart
VM logs configuration
You have to connect to the VM, edit the winlogbeats.yml and do some commands
- Connect to the VM (you have the IP adress on the health.php page or you can do
sudo VBoxManage guestproperty get sandbox "/VirtualBox/GuestInfo/Net/0/V4/IP") - Open an Administrator Powershell Prompt and go to this folder :
cd ‘C:\Program Files\winlogbeat’
- Open the file
C:\Program Files\winlogbeatwith notepadd or other Change : the password at “password:” (put the password you have in admin.txt) Replace All the Ip that corresponding to 192.168.142.130 with the address of your ELK server the ca_trusted_fingerprint: (to have it, run this command in the purplelab server :sudo openssl x509 -fingerprint -sha256 -in /etc/elasticsearch/certs/http_ca.crtand REMOVE THE “:” characters with this commandecho "$Yourfingerprint" | tr -d ':') - test the configuration with :
& “C:\Program Files\Winlogbeat\winlogbeat.exe” test config -c “C:\Program Files\Winlogbeat\winlogbeat.yml” -e
- If the configuration is OK, set up assets with the following command :
.\winlogbeat.exe setup -e
- Start the Winlobeat Service :
Start-Service winlogbeat
- ⚠️ On the purplelab server, Make a snapshot of the vm -> named: “Snapshot1”
sudo VBoxManage snapshot “sandbox” take “Snapshot1” –description “snapshot before the mess”
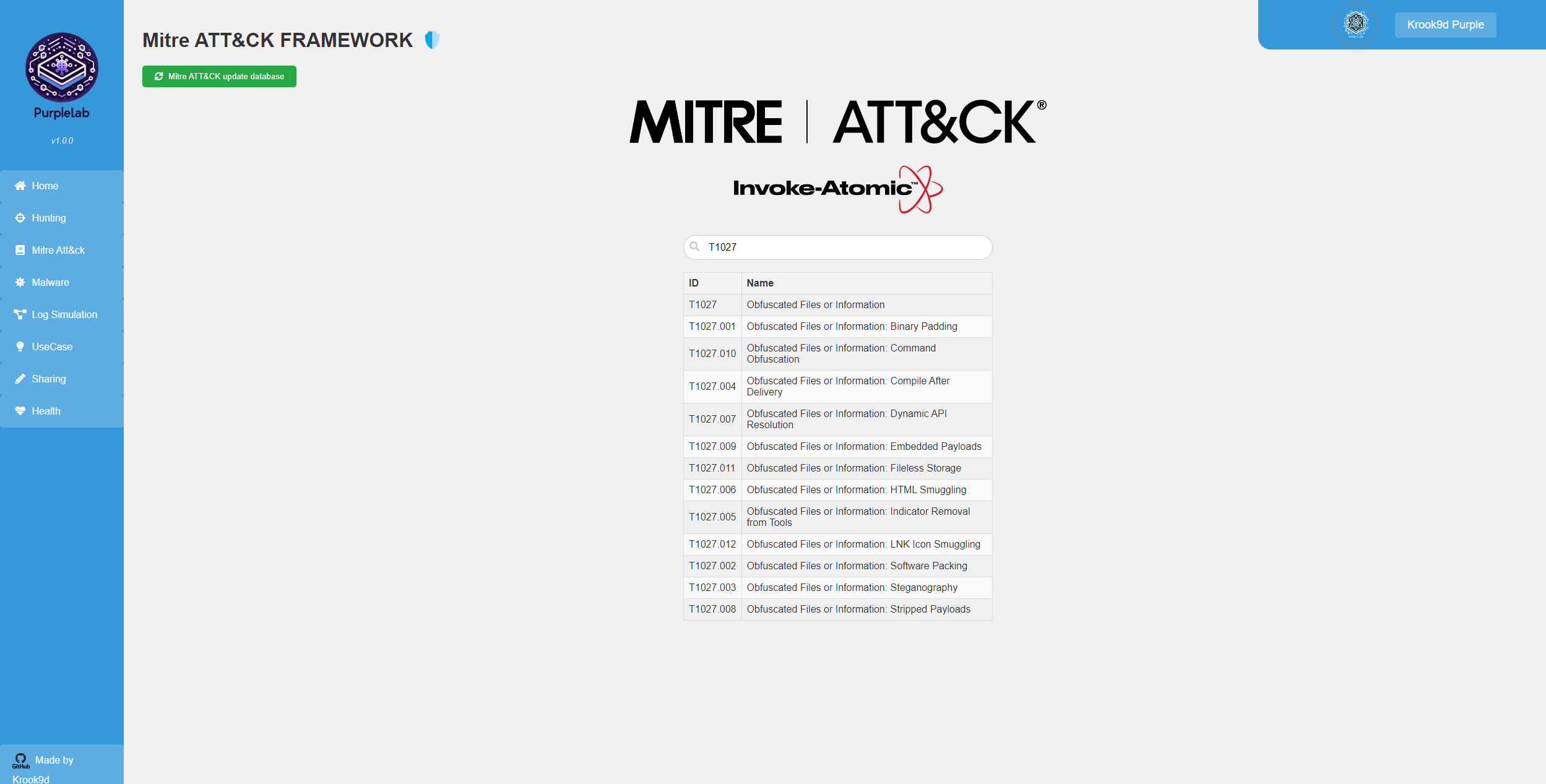
⚠️ After that, and once you’ve finished configuring the elastic search server, check if the service is running, go to kibana (Hunting page on Purplelab), click on the Discover tab, normally, you will see the Windows event from the VM. Indicators in the home page should be fed
Usage
Make sure that de VM is running :sudo VBoxManage showvminfo sandbox –machinereadable | grep “VMState=” | awk -F'”‘ ‘{print $2}’
If not, do :sudo VBoxManage startvm sandbox –type headless
Open a new prompt on the PurpleLab server and start the flask server on :sudo python3 /home/$(logname)/app.py
Once the application is fully configured lets explain all the pages and the features


What do you think?
Show comments / Leave a comment