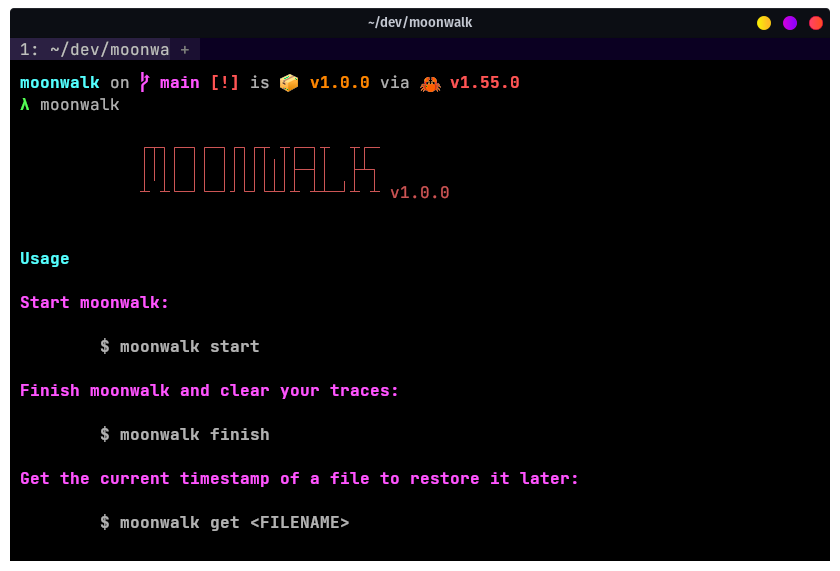
https://github.com/Aditya-dom/moonwalk-back
Cover your tracks during Linux Exploitation by leaving zero traces on system logs and filesystem timestamps.
moonwalk-back is a 400 KB single-binary executable that can clear your traces while penetration testing a Unix machine. It saves the state of system logs pre-exploitation and reverts that state including the filesystem timestamps post-exploitation leaving zero traces of a ghost in the shell.
⚠️ NOTE: This tool is open-sourced to assist solely in Red Team operations and in no means is the author liable for repercussions caused by any prohibited use of this tool. Only make use of this in a machine you have permission to test.
Features
- Small Executable: Get started quickly with a
curlfetch to your target machine. - Fast: Performs all session commands including logging, trace clearing, and filesystem operations in under 5 milliseconds.
- Reconnaissance: To save the state of system logs,
moonwalk-backfinds a world-writable path and saves the session under a dot directory which is removed upon ending the session. - Shell History: Instead of clearing the whole history file,
moonwalk-backreverts it back to how it was including the invokation ofmoonwalk-back. - Filesystem Timestamps: Hide from the Blue Team by reverting the access/modify timestamps of files back to how it was using the
GETcommand.
Installation
$ curl -L https://github.com/aditya-dom/moonwalk-back/releases/download/v1.0.0/moonwalk-back_linux -o moonwalk-back
(AMD x86-64)
OR
Download the executable from Releases OR Install with cargo:
$ cargo install --git https://github.com/aditya-dom/moonwalk-back.git

What do you think?
Show comments / Leave a comment