December 16, 2024By Prapattimynk
Install Or download from releases after installation run cent init to initialize cent with the configuration files you find here Supported commands Command Description check Check if templates repo are still available init Cent init configuration file summary Print summary table update Update your repository validate Validate templates, if the template is invalid it is
December 16, 2024By Prapattimynk
Improved Speed & Efficiency: Significantly faster and smoother DNS brute-forcing with lightweight resource usage. Memory & Resource Management: Optimized to handle large-scale DNS scans without consuming excessive system resources. Flexible Input: Supports both stdin and file-based domain lists for DNS brute-forcing. Concurrency Control: Rate limiting and concurrency management to ensure stable performance under heavy loads.
June 26, 2024By Prapattimynk
Installation pip install git+https://github.com/blacklanternsecurity/trevorproxy See the accompanying Blog Post for a fun rant and some cool demos! A SOCKS proxy written in Python that randomizes your source IP address. Round-robin your evil packets through SSH tunnels or give them billions of unique source addresses! TREVORproxy IPv6 Subnet Proxy Diagram TREVORproxy SSH Proxy Demo TREVORproxy Subnet
June 26, 2024By Prapattimynk
A program to dub multi-lingual media and anime using modern AI speech synthesis, diarization, language identification, and voice cloning. Download Release 1.0 You can try the first binary version which has access to basic dubbing features with the non-AI based libraries for Windows and Linux. This is a good way to try out the program
June 21, 2024By Prapattimynk
Most web application firewalls (WAFs) have limitations for how much data they can process when a request body is sent. This means for HTTP requests that contain a request body (i.e. POST, PUT, PATCH etc), it is usually possible to bypass the WAF by simply prepending junk data. When the request is padded with this
June 21, 2024By Prapattimynk
SafeLine is a web security gateway to protect your websites from attacks and exploits. It defenses for all of web attacks, such as sql injection, code injection, os command injection, CRLF injection, ldap injection, xpath injection, rce, xss, xxe, ssrf, path traversal, backdoor, bruteforce, http-flood, bot abused and so on. 🏠Home | 📖Documentation
June 21, 2024By Prapattimynk
Content Introduction Architecture Demo pages Requirements Quick start Administrator’s guide Sensor Server User’s guide Reporting interface Real-life cases Mass scans Anonymous attackers Service attackers Malware Suspicious domain lookups Suspicious ipinfo requests Suspicious direct file downloads Suspicious HTTP requests Port scanning DNS resource exhaustion Data leakage False positives Best practice(s) License Sponsors Developers Presentations Publications Blacklist
June 18, 2024By Prapattimynk
403JUMP is a tool designed for penetration testers and bug bounty hunters to audit the security of web applications. It aims to bypass HTTP 403 (Forbidden) pages using various techniques. Features Multiple Bypass Techniques Including: Different HTTP Verbs Different Headers Path Fuzzing. Customization: Allows customization of headers and cookies for more targeted testing. Concurrency: Performs
June 17, 2024By Prapattimynk
About – v3.6 This is a Chrome/Firefox Extension that can do the following: The ability to show an alert for reflected parameters was inspired by a comment by @renniepak on Episode 42 of the Critical Thinking – Bug Bounty Podcast where he mentioned he had his own browser extension that let him know about any
June 17, 2024By Prapattimynk
A new approach to Browser In The Browser (BITB) without the use of iframes, allowing the bypass of traditional framebusters implemented by login pages like Microsoft. This POC code is built for using this new BITB with Evilginx, and a Microsoft Enterprise phishlet. Before diving deep into this, I recommend that you first check my
June 16, 2024By Prapattimynk
With Cassowary you can run a Windows virtual machine and use Windows applications on Linux as if they were native applications, built upon FreeRDP and remote apps technology. If you prefer a setup guide video instead of a wall of text, click here. Please give a star ⭐ or follow this project if you find
June 16, 2024By Prapattimynk
What is keyFinder? keyFinder is chrome extension that searches the DOM for any embedded script link, as script tag may contain keys for specific API(such as Google maps API) and you can add keywords to search for it at any website you visit. Features: it searches the DOM for “src” of scripts and see if
June 14, 2024By Prapattimynk
SQL – Structured Query Language ¶‣ Advanced SQL Injection for AWAE Goal is to master SQL Injection Discovery, Detection and Exploitation Footnotes: Advanced SQL Injection Cheatsheet Rigorous Google Dorking Reddit Dorking Web Security Academy – SQL Injection My Brain + My Experience + My Logic Table of Content - Learning a lil' bit of SQL
June 14, 2024By Prapattimynk
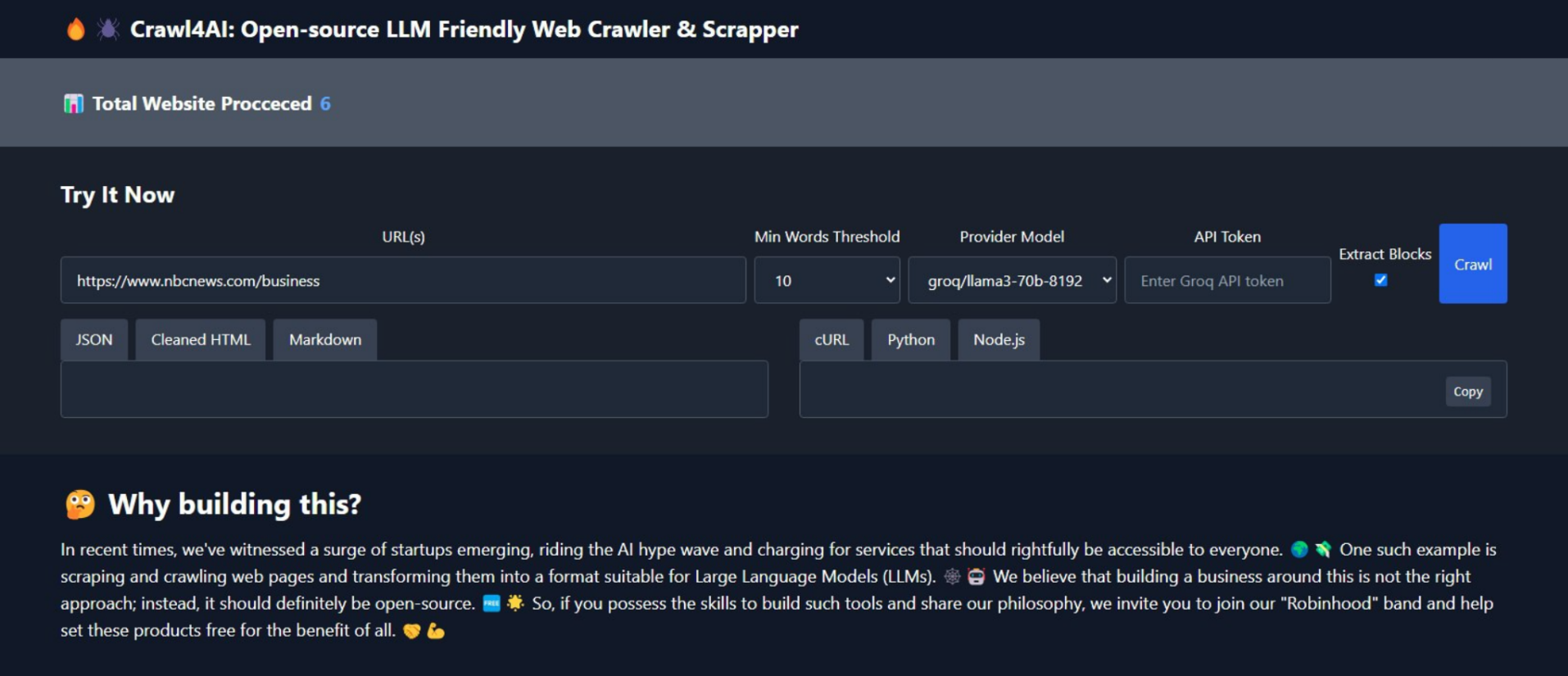
Crawl4AI v0.2.3 🕷️🤖 Crawl4AI has one clear task: to simplify crawling and extract useful information from web pages, making it accessible for large language models (LLMs) and AI applications. 🆓🌐 Use as REST API: Check Use as Python library: Recent Changes v0.2.3 🎨 Extract and return all media tags (Images, Audio, and Video). Check result.media
June 14, 2024By Prapattimynk
IconJector This is a Windows Explorer DLL injection technique that uses the change icon dialog on Windows. https://github.com/0xda568/IconJector/assets/61665703/bbf53775-ad8d-422b-b186-663ff5074976 How does it work? Firstly, a folder is created in the temp directory, and the properties of the folder are opened using SHObjectProperties. To retrieve the handle of the window independently of the system language, EnumWindows is
June 14, 2024By Prapattimynk
Project that generates Malicious Office Macro Enabled Dropper for DLL SideLoading and Embed it in Lnk file to bypass MOTW Install requirements pip install -r requirements.txt Video Demonstration https://github.com/SaadAhla/dropper/assets/123980007/7db05d2c-05e5-4a70-b967-6faecd7a296e Direct View On Github