https://github.com/Hackmanit/TInjA
Features
- Automatic detection of template injection possibilities and identification of the template engine in use.
- 44 of the most relevant template engines supported (see Supported Template Engines).
- Both SSTI and CSTI vulnerabilities are detected.
- SSTI = server-side template injection
- CSTI = client-side template injection
- Efficient scanning thanks to the usage of polyglots:
- On average only five polyglots are sent to the web page until the template injection possibility is detected and the template engine identified.
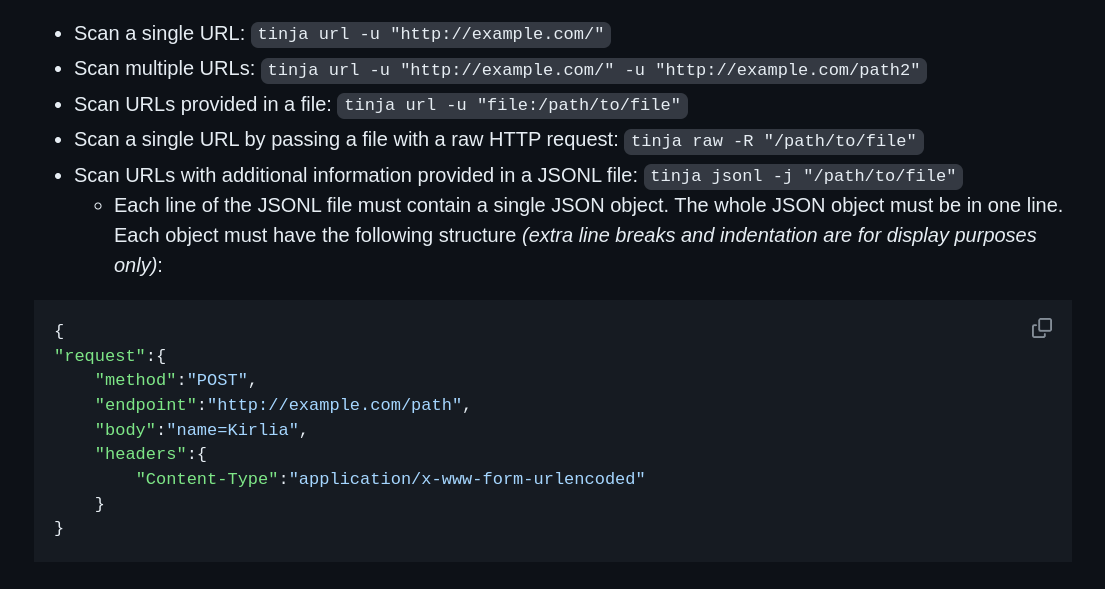
- Pass crawled URLs to TInjA in JSONL format.
- Pass a raw HTTP request to TInjA.
- Set custom headers, cookies, POST parameters, and query parameters.
- Route the traffic through a proxy (e.g., Burp Suite).
- Configure Ratelimiting.
Supported Template Engines
.NET
- DotLiquid
- Fluid
- Razor Engine
- Scriban
Elixir
- EEx
Go
- html/template
- text/template
Java
- Freemarker
- Groovy
- Thymeleaf
- Velocity
JavaScript
- Angular.js
- Dot
- EJS
- Eta
- Handlebars
- Hogan.js
- Mustache
- Nunjucks
- Pug
- Twig.js
- Underscore
- Velocity.js
- Vue.js
PHP
- Blade
- Latte
- Mustache.php
- Smarty
- Twig
Python
- Chameleon
- Cheetah3
- Django
- Jinja2
- Mako
- Pystache
- SimpleTemplate Engine
- Tornado
Ruby
- ERB
- Erubi
- Erubis
- Haml
- Liquid
- Mustache
- Slim
Installation
Option 1: Prebuilt Binary
Prebuilt binaries of TInjA are provided on the releases page.
Option 2: Install Using Go
Requirements: go1.21 or higher
go install -v github.com/Hackmanit/TInjA@latest


What do you think?
Show comments / Leave a comment